This post is a companion to the following GitHub repository:https://github.com/gbaeke/aks-traefik-azure-deploy. The repository contains ARM templates to deploy an AD integrated Kubernetes cluster and an IP address plus a Helm chart to deploy Traefik. Traefik is configured to use the deployed IP address. In addition to those files, the repository also contains the YAML pipeline, ready to be imported in Azure DevOps.
Let’s take a look at the different building blocks!
AKS ARM Template
The aks folder contains the template and a parameters file. You will need to modify the parameters file because it requires settings to integrate the AKS cluster with Azure AD. You will need to specify:
- clientAppID: the ID of the client app registration
- serverAppID: the ID of the server app registration
- tenantID: the ID of your AD tenant
Also specify clientId, which is the ID of the service principal for your cluster. Both the serverAppID and the clientID require a password. The passwords have been set via a pipeline secret variable.
The template configures a fairly standard AKS cluster that uses Azure networking (versus kubenet). It also configures Log Analytics for the cluster (container insights).
Deploying the template from the YAML file is done with the task below. You will need to replace YOUR SUBSCRIPTION with an authorized service connection:
# DEPLOY AKS IN TEST
- task: AzureResourceGroupDeployment@2
inputs:
azureSubscription: 'YOUR SUBSCRIPTION'
action: 'Create Or Update Resource Group'
resourceGroupName: '$(aksTestRG)'
location: 'West Europe'
templateLocation: 'Linked artifact'
csmFile: 'aks/deploy.json'
csmParametersFile: 'aks/deployparams.t.json'
overrideParameters: '-serverAppSecret $(serverAppSecret) -clientIdsecret $(clientIdsecret) -clusterName $(aksTest)'
deploymentMode: 'Incremental'
deploymentName: 'CluTest' The task uses several variables like $(aksTestRG) etc… If you check azure-pipelines.yaml, you will notice that most are configured at the top of the file in the variables section:
variables: aksTest: 'clu-test' aksTestRG: 'rg-clu-test' aksTestIP: 'clu-test-ip'
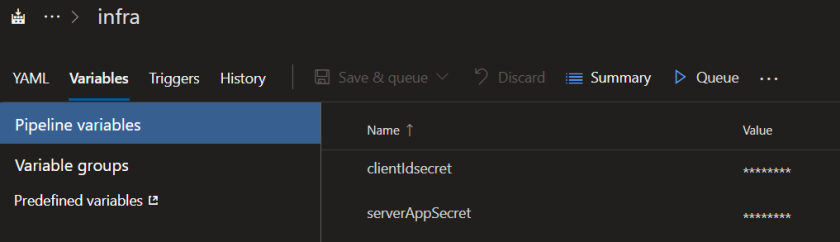
The two secrets are the secret variables. Naturally, they are configured in the Azure DevOps UI. Note that there are other means to store and obtain secrets, such as Key Vault. In Azure DevOps, the secret variables can be found here:
IP Address Template
The ip folder contains the ARM template to deploy the IP address. We need to deploy the IP address resource to the resource group that holds the AKS agents. With the names we have chosen, that name is MC_rg-clu-test_clu-test_westeurope. It is possible to specify a custom name for the resource group.
Because we want to obtain the IP address after deployment, the ARM template contains an output:
"outputs": {
"ipaddress": {
"type": "string",
"value": "[reference(concat('Microsoft.Network/publicIPAddresses/', parameters('ipName')), '2017-10-01').ipAddress]"
}
} The output ipaddress is of type string. Via the reference template function we can extract the IP address.
The ARM template is deployed like the AKS template but we need to capture the ARM outputs. The last line of the AzureResourceGroupDeployment@2 that deploys the IP address contains:
deploymentOutputs: 'armoutputs'
Now we need to extract the IP address and set it as a variable in the pipeline. One way of doing this is via a bash script:
- task: Bash@3
inputs:
targetType: 'inline'
script: |
echo "##vso[task.setvariable variable=test-ip;]$(echo '$(armoutputs)' | jq .ipaddress.value -r)" You can set a variable in Azure DevOps with echo ##vso[task.setvariable variable=variable_name;]value. In our case, the “value” should be the raw string of the IP address output. The $(armoutputs) variable contains the output of the IP address ARM template as follows:
{"ipaddress":{"type":"String","value":"IP ADDRESS"}}
We now have the IP address in the test-ip variable, to be used in other tasks via $(test-ip).
Taking care of the prerequisites
In a later phase, we install Traefik via Helm. So we need kubectl and helm on the build agent. In addition, we need to install tiller on the cluster. Because the cluster is RBAC-enabled, we need a cluster account and a role binding as well. The following tasks take care of all that:
- task: KubectlInstaller@0
inputs:
kubectlVersion: '1.13.5'
- task: HelmInstaller@1
inputs:
helmVersionToInstall: '2.14.1'
- task: AzureCLI@1
inputs:
azureSubscription: 'YOUR SUB'
scriptLocation: 'inlineScript'
inlineScript: 'az aks get-credentials -g $(aksTestRG) -n $(aksTest) --admin'
- task: Bash@3
inputs:
filePath: 'tiller/tillerconfig.sh'
workingDirectory: 'tiller/' Note that we use the AzureCLI built-in task to easily obtain the cluster credentials for kubectl on the build agent. We use the –admin flag to gain full access. Note that this downloads sensitive information to the build agent temporarily.
The last task just runs a shell script to configure the service account and role binding and install tiller. Check the repository to see the contents of this simple script. Note that this is the quick and easy way to install tiller, not the most secure way!
Install Traefik and use the IP address
The repository contains the downloaded chart (helm fetch stable/traefik –untar). The values.yaml file was modified to set the ingressClass to traefik-ext. We could have used the chart from the Helm repository but I prefer having the chart in source control. Here’s the pipeline task:
- task: HelmDeploy@0
inputs:
connectionType: 'None'
namespace: 'kube-system'
command: 'upgrade'
chartType: 'FilePath'
chartPath: 'traefik-ext/.'
releaseName: 'traefik-ext'
overrideValues: 'loadBalancerIP=$(test-ip)'
valueFile: 'traefik-ext/values.yaml' kubectl is configured to use the cluster so connectionType can be set to ‘None’. We simply specify the IP address we created earlier by setting loadBalancerIP to $(test-ip) with the overrides for values.yaml. This sets the loadBalancerIP setting in Traefik’s service definition (in the templates folder). Service.yaml in the templates folder contains the following section:
spec:
type: {{ .Values.serviceType }}
{{- if .Values.loadBalancerIP }}
loadBalancerIP: {{ .Values.loadBalancerIP }}
{{- end }} Conclusion
Deploying AKS together with one or more public IP addresses is a common scenario. Hopefully, this post together with the GitHub repo gave you some ideas about automating these deployments with Azure DevOps. All you need to do is create a pipeline from the repo. Azure DevOps will read the azure-pipelines.yml file automatically.
About the Author:
Geert has been active in the field of infrastructure and application architecture for over 20 years. As co-founder and managing partner of Inity, he advises customers on their path to modernize their infrastructure and application stack in the cloud.
Reference:
Baeke, G. (2019). Deploy AKS and Traefik with an Azure DevOps YAML pipeline. Available at:
https://blog.baeke.info/2019/07/02/deploy-aks-and-traefik-with-an-azure-devops-yaml-pipeline/ [Accessed: 26th July 2019].