
Behind the scenes in Galway: Building the ESPC25 programme
Blog PostsThere’s something special about getting together in person to shape what’s going to become an unforgettable conference experience, and this year, that something happened in the beautiful city of Galway. The ESPC25 Programme Team met on-site to go through hundreds (!) of session submissions. Yes, hundreds. With over 85 community sessions, 10 full day tutorials,… READ MORE

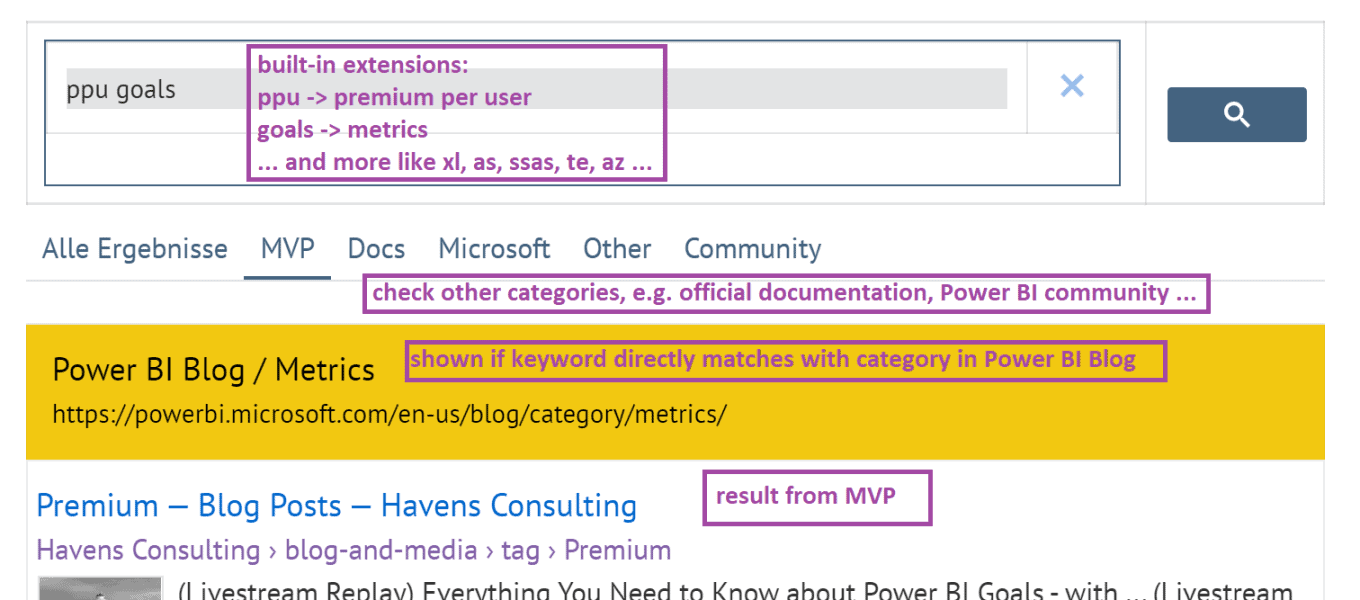

 ! Introduction Remember that mysterious squiggly line we encountered in our previous article?, The one that had us wondering and
! Introduction Remember that mysterious squiggly line we encountered in our previous article?, The one that had us wondering and
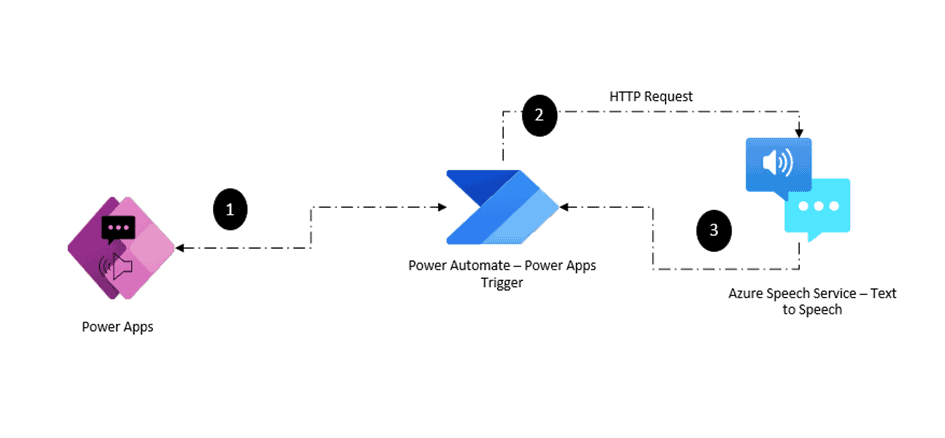
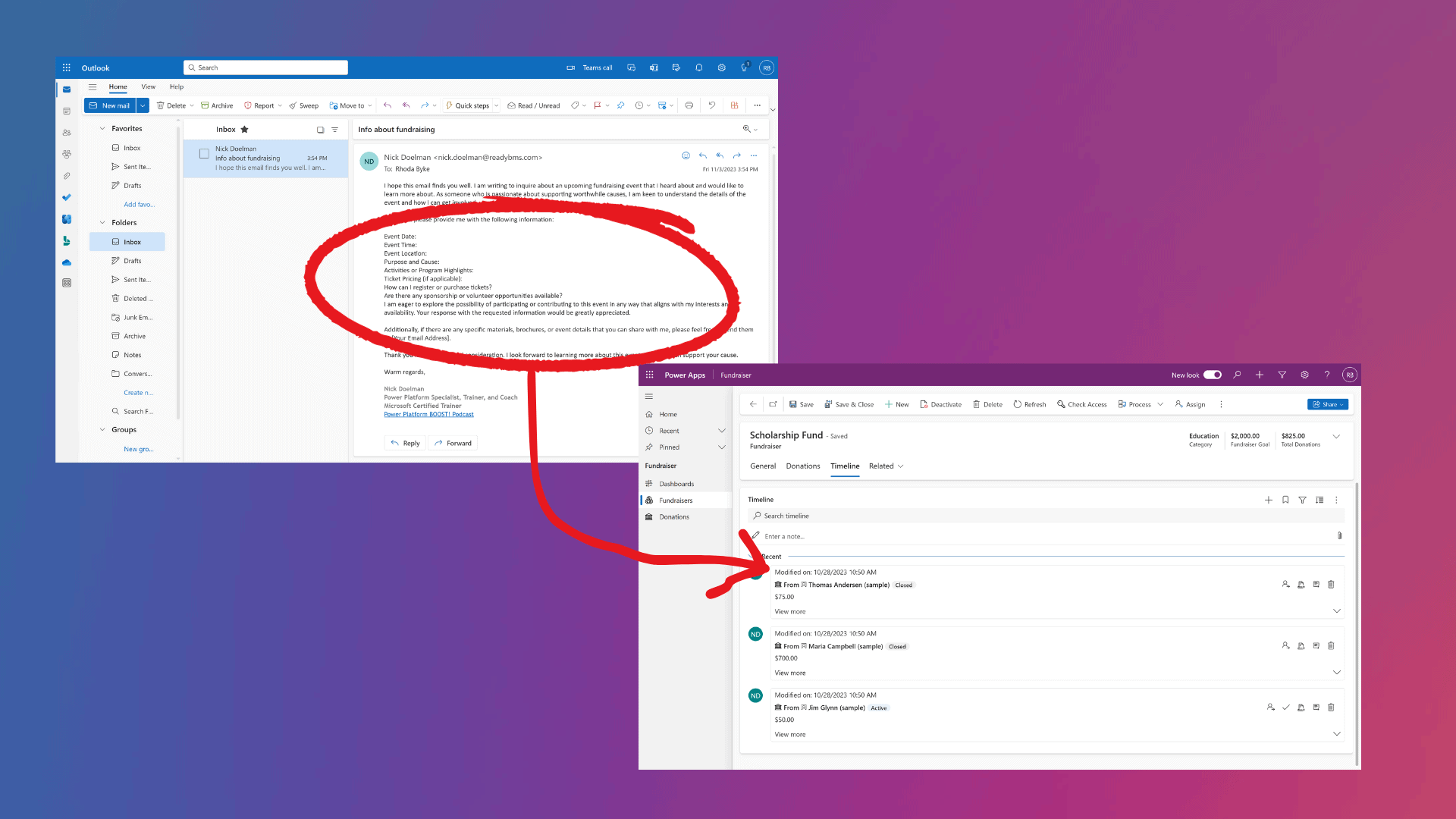

![[Whitepaper] Proactive Defense from Tomorrow's Cyber Threats [Whitepaper] Proactive Defense from Tomorrow's Cyber Threats](https://www.sharepointeurope.com/wp-content/uploads/2023/11/Proactive-Defense-from-Tomorrows-Cyber-Threats.png)
