In my previous article, I introduced Azure Sentinel basic configuration and different connector options as office 365. Another type of connector will be shown in this article which is the Palo Alto connector. This is one of the rich features of Azure Sentinel by having different connectors to Microsoft as well as another 3rd party solutions.
WHY PALO ALTO CONNECTOR WITH AZURE SENTINEL CONNECTOR ?
The power of any SIEM whether its traditional or cloud SIEM as Sentinel is to aggregate and collect logs from multiple different sources. On the other hand the Firewall device on the edge of your corporate network is an ideal candidate. All company traffic in both directions will pass by the firewall for all internal users. Passing this traffic to the Sentinel SIEM allows you to smoothly run queries and analytics on these logs. Remember the main idea is to connect all sources of traffic and user actions to Sentinel for analysis.
The process of connecting Palo Alto Firewall to Azure Sentinel SIEM is straight forward. First you need to have a syslog agent machine or VM which can be on-premise or created on the cloud. Microsoft configuration can automatically create one for you on Azure Sentinel Workspace. Secondly you need to forward the logs from the firewall box or virtual machine to the syslog machine created earlier. Finally you will need to validate the connection if it didn’t work after configuration.
AZURE SENTINEL AND PALO ALTO CONNECTOR CONFIGURATION
- First we need to add a new connector to the Azure Sentinel for the Palo Alto device. Navigate to the Azure Sentinel – Connectors
- Choose the Palo Alto Networks and Click on Configure

SYSLOG CONFIGURATION, AUTOMATIC OR MANUAL ?
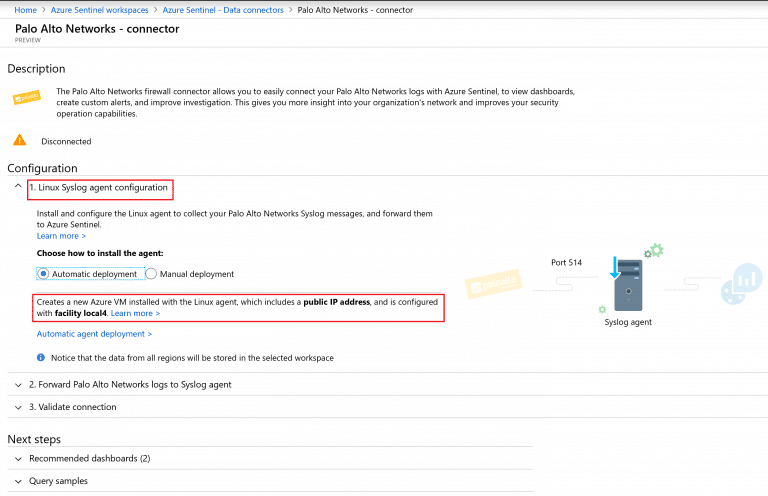
- The first step of the configuration will be the Syslog. As i mentioned earlier you can have it on-premise or on the cloud. If there is an existing on-premise syslog server then you will pick manual and go with the steps to install the Sentinel agent. In our case/demo I will go with Automatic deployment. Click on Automatic agent deployment. This will move us to create a new VM which will be used as the syslog machine preloaded with Sentinel VM (Automatically). Furthermore will start this machine and provide you with needed details as IP address. Take a note that this machine Facility is Local4.
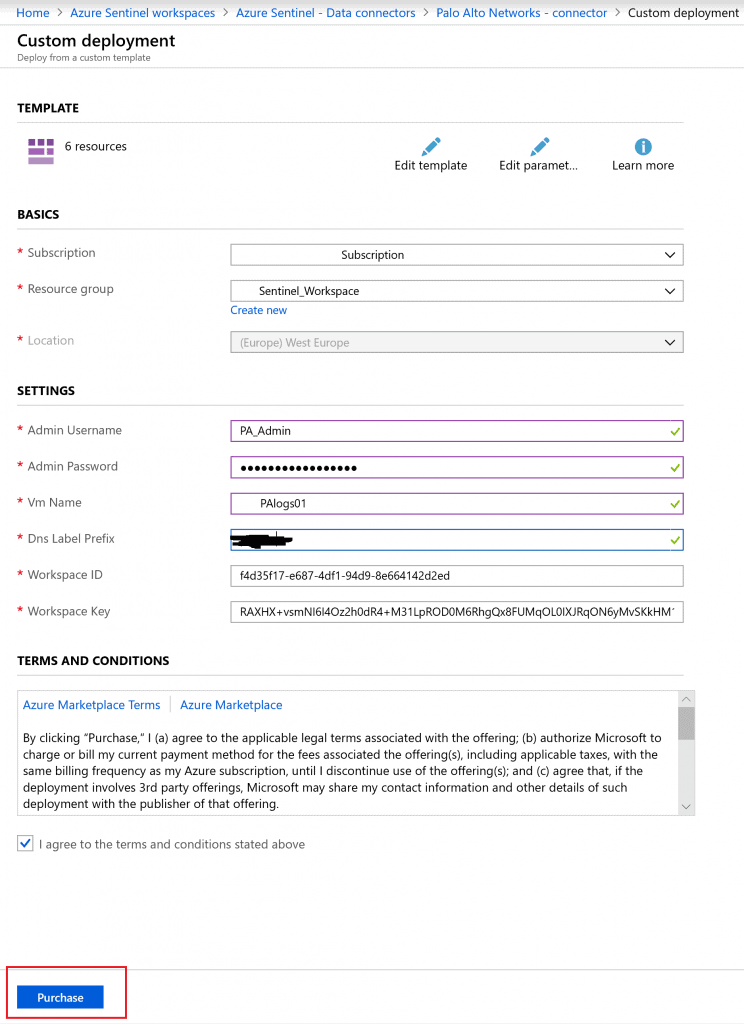
- Automatic deployment will direct you to creating new virtual machine template. Make sure to pick your subscription and resource group pointing to the Sentinel workspace. Create a name, admin username and password for the VM. This is important later for validation and any troubleshooting. Finally click on Purchase
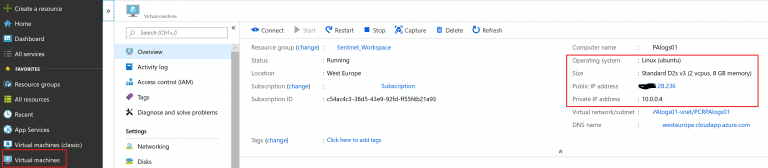
- Next from your Azure portal navigate to Virtual Machines. Open the Virtual machines that was created in the previous step. Make sure its in the Sentinel Workspace, secondly take a note with its public IP. Finally ensure its up and running.
- Now its time to switch to our PaloAlto Firewall device. Go to device then Syslog to configure our Syslog settings
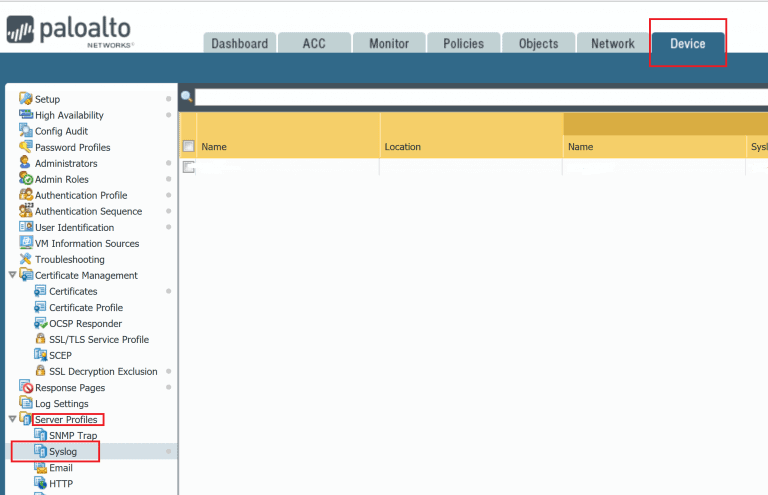
- Create a new syslog profile for Sentinel forwarding. In the Syslog server add the public IP address of your Syslog agent VM. Finally ensure you are using BSD format and facility Local4.
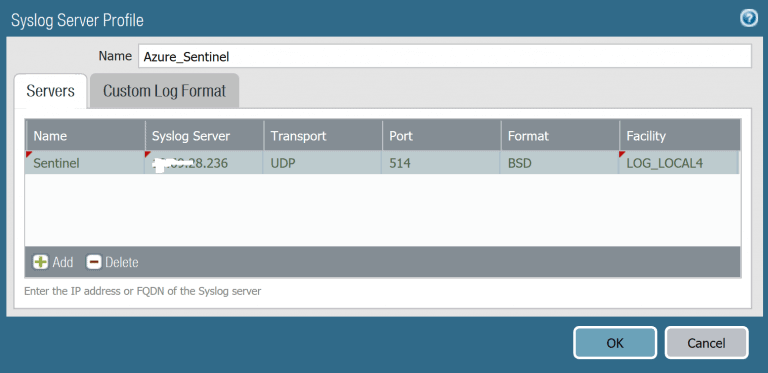
CEF CUSTOM LOG FORMAT
- Click on Custom Log format. This is a tricky and critical step to get your logs on Azure Sentinel. First we need to configure PaloAlto to send the Logs in CEF format in order to be proceed in Azure Sentinel Syslog. For more info please check PaloAlto CEF configuration guides here. Pick the guide that matches your PaloAlto Operating system. I picked the latest version OS version 8.0 and on page 10 you can find examples of CEF format. Next you need to copy each custom format to your log type (For example Threat or Traffic Log type as shown below).
- However as per Microsoft recommendation and my experience, direct copy from PDF will corrupt some data. Few characters might get missed or replaced. So you need to check them carefully after the copy to ensure the syntax is correct. I found few blogs and sites with clear text CEF formats that you can copy instead of the PDF. For example IBM Syslog configuration for PaloAlto. Its very handy and you can copy directly from it. CEF is a common Event Format with most devices using it. Finally you will hit Ok to save your settings.
- Next you need to go to Objects – Log Forwarding. Create a new Log forwarding rule to forward logs to our Azure Sentinel Syslog profile create earlier.

- In the Log profile details, configure your log type and filer. This will specify which logs will be sent to Sentinel. Pick the log type that you have configure the custom CEF format earlier. These are the ones that can show up in Azure sentinel.
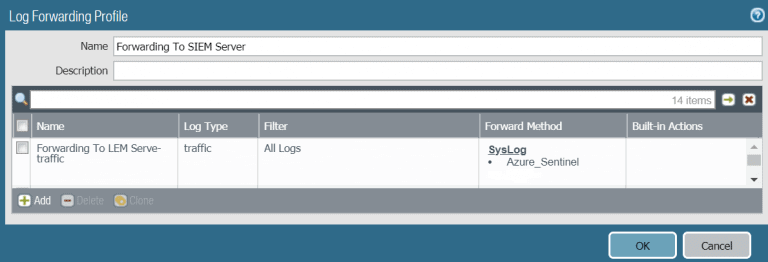
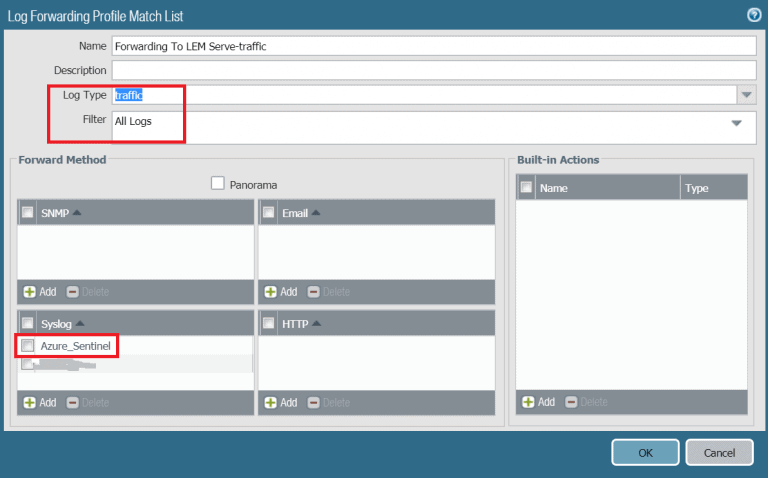
SYSLOG FORWARDING PROFILE
- Next we need to assign this log forwarding profile to our Security rules. Move to Policies then security. Typically i would select the most general security policy applied to all users accessing the internet. Remember we need to get all traffic going out from the Palo Alto device to be sent to Azure Sentinel.
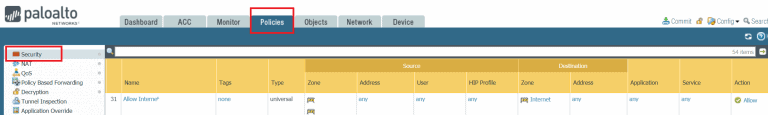
- In the Security Policy actions. Ensure the Log forwarding rule is pointing to the log forwarding profile created earlier. This Log forwarding profile contains all Azure Sentinel settings. Finally Click Ok then Commit. We are done from the Firewall part of configuration.
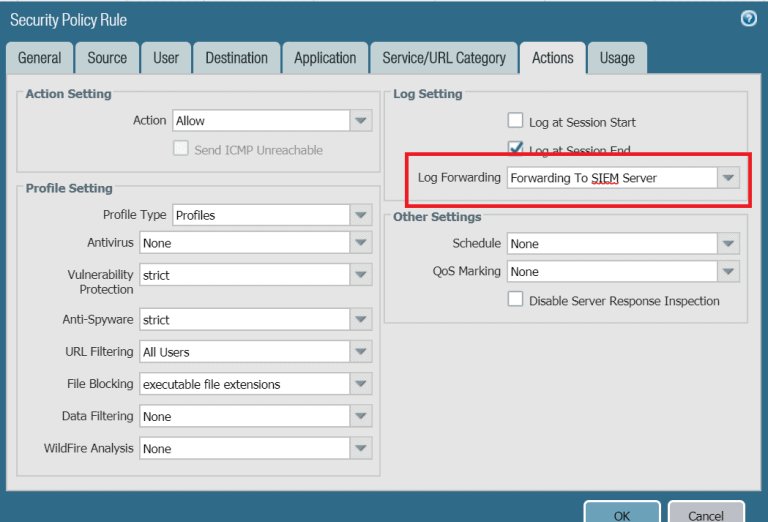
- Moving back to the Azure Sentinel Palo Alto connector. Give it some time around 1 hour, if its not shown as connected then you can move to step 3 which is validating the connection for troubleshooting.
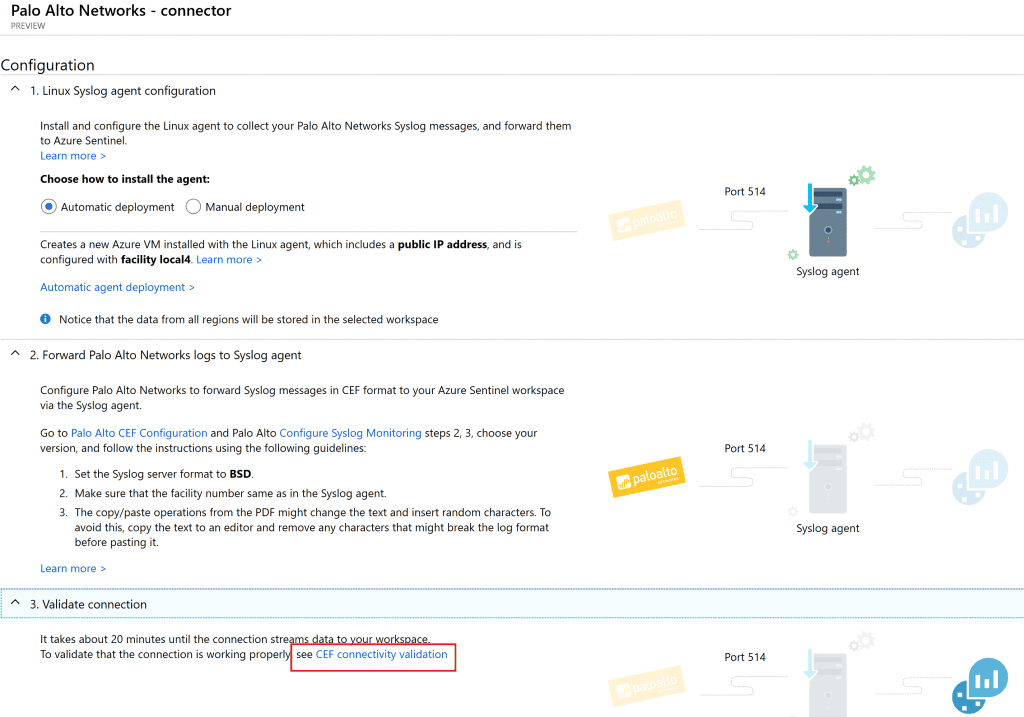
- In my case there was one missing thing that need to get configured and checked. Go to the Azure Sentiel Workspace settings – then Advanced settings – Data – Syslog. Ensure the Facility configured for this workspace is Local4. In my case there were nothing displayed. So i added Local4, ensure all logs are enabled and saved it.
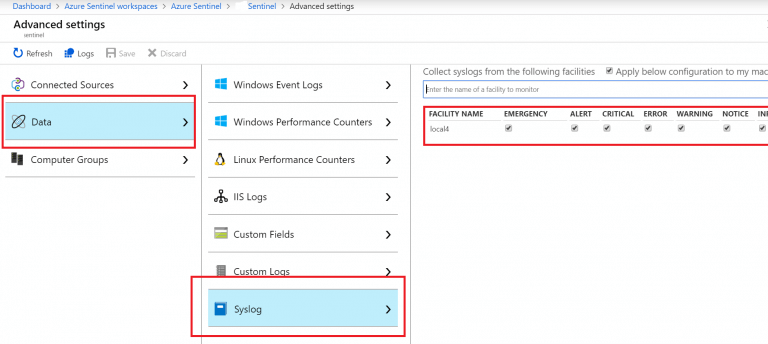
That should do the trick and setup your Palo Alto connector. Finally you can install the Palo Alto Dashboards and give it some time to see the logs flying to your Sentinel Workspace.
CONCLUSION
I like the idea of having out of the box connectors available for the Azure Sentinel SIEM. This enriches my SIEM dashboard and connect all critical traffic to Sentinel. This will allow further analysis and investigations. Remember Azure Sentinel is in Preview and free of charge for now. Why waiting ? go ahead and give it a try.
Hopefully this post was informative and till we meet on another Azure Sentinel article.
Find out more about Azure @ ESPC19 here
I am an IT professional specialized in IT infrastructure, security and IT management.
My real passion is Networking and Security. I hold a BS, MS, MCITP, MCSE, CCNP, CWSP, CEH, CHFI, ITIL and PMP.
I have been awarded the Microsoft Most Valuable Professional (MVP) in Enterprise Security
Reference:
Mahmoud Nabil, A (2019). Azure Sentinel Connector with Palo Alto Firewalls. Available at: https://itcalls.net/azure-sentinel-connector-with-palo-alto-firewalls/ [Accessed: 8th October 2019].







 Using a SharePoint Online list as a Knowledge source via ACTIONS in Copilot AI Studio
Using a SharePoint Online list as a Knowledge source via ACTIONS in Copilot AI Studio
