You’re a cloud operator for an Azure Stack Integrated system and for whatever reason you have the task of deploying the App Services Resource provider…
In this blog series, I’m going to take you through the considerations and deployment process of the App Services resource provider on an Azure Stack Integrated System. This should work on an ASDK but you’re probably going to make life tough for your single server instance.
Other posts in this series:
Highly Available App Service 1.4 on Azure Stack – Step 1: Design and planning
Highly Available App Service 1.4 on Azure Stack – Step 2: Deployment (this post)
Highly Available App Service 1.4 on Azure Stack – Step 3: Post-deployment setup (in process)
Highly Available App Service 1.4 on Azure Stack – Step 4: Updating App Service (in process)
Before we get into the nitty-gritty of it all, you should go an validate some marketplace items and if you don’t have them available you should kick off some marketplace downloads now…
- Windows Server 2016 Datacenter Core Image
- SQL Server 2016 SP2 on Windows Server 2016
- Latest SQL IaaS Extension 1.2.x (currently 1.2.30)
- Latest PowerShell Desired State Configuration Extension (currently 2.76.0)
Done? Welcome back
If you’re the studious type, then you’re probably going to get by with just the Microsoft documentation on this process, as these days it is fantastic and continually getting better. The last thing I want to do is reinvent the wheel and fill the internet up with another duplicated blog, but for those who want the perspective of a Cloud Operator who has deployed and is managing a production Azure Stack Integrated System perspective, then this blog is for you…
Firstly there are some assumptions made prior to embarking on this journey. It is assumed that:
- You know what Azure Stack is…
- You’re the Cloud Operator for an Azure Stack Integrated System
- You have a fundamental understanding of what App Services is
- Appropriate certificates have been sourced
Environment summary:
This blog series is based on an 4-node Azure Stack Integrated System that is Connected to Azure with Azure Active Directory as the Identity provider.
Deployment Steps:
- Setup deployment environment
- Create Azure AD application
- Deploy HA File & SQL environment
- Run the App Service 1.4 installer
Ok, let’s get started
1. Setup deployment environment
Cloud Operator VM
Prior to doing anything, we need to setup our deployment environment. I recommend this to be your Cloud Operator VM. You have a one of these right:
On my Cloud Operator VMI create a working folder for all resource providers and a subfolder for each RP: i.e. C:\AzureStack-RPs\AppService. I will refer to this as the working folder.
Installer sources
First step is to have a read of this doc. It covers many of the considerations you need to make prior to pressing the deploy button:
App Service: Before you get started
https://docs.microsoft.com/en-us/azure/azure-stack/azure-stack-app-service-before-you-get-started
Essentially download (links in the above docs page) to your working folder:
App Service on Azure Stack deployment helper scripts
App Service on Azure Stack installer
Root certificate
Export the Azure Resource Manager root certificate for Azure Stack and save to the working folder.
Azure Resource Manager
PaaS certificates
Save your PaaS certificates to the working folder. If you don’t have these yet, stop what you’re doing and go read this blog post. I created a certs folder in the working folder and saved them all there.
Save your certs in one folder
2. Create an Azure Active Directory application
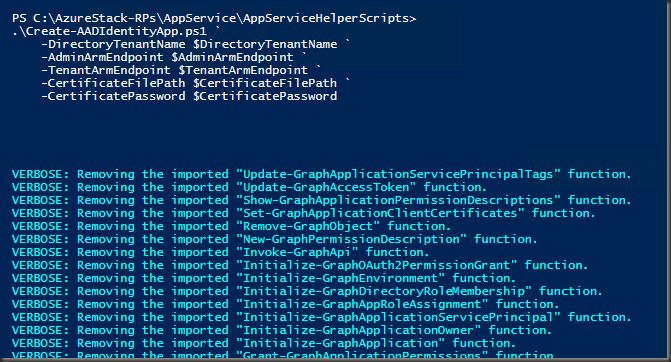
Use the script in the App Service helper files
cd C:\AzureStack-RPs\AppService\AppServiceHelperScripts
$DirectoryTenantName = 'tenantname.onmicrosoft.com'
$AdminArmEndpoint = 'adminmanagement.region.domain.com'
$TenantArmEndpoint = 'management.region.domain.com'
$CertificateFilePath = "C:\AzureStack-RPs\AppService\certs\sso.appservice.region.domain.com.pfx"
$CertificatePassword = '$mascerts123' | ConvertTo-SecureString -AsPlainText -Force
.\Create-AADIdentityApp.ps1 `
-DirectoryTenantName $DirectoryTenantName `
-AdminArmEndpoint $AdminArmEndpoint `
-TenantArmEndpoint $TenantArmEndpoint `
-CertificateFilePath $CertificateFilePath `
-CertificatePassword $CertificatePassword
All things being equal you should see something like the below when started
You’ll get prompted to authenticate to the directory tenant. Provide the details of a user with access to create Applications in the directory.
Enter the password

Copy the App ID info down, you’ll need it later
Now we need to grant the application permissions for the App Service application to the accounts in Active Directory.
In the portal, find the newly created application.
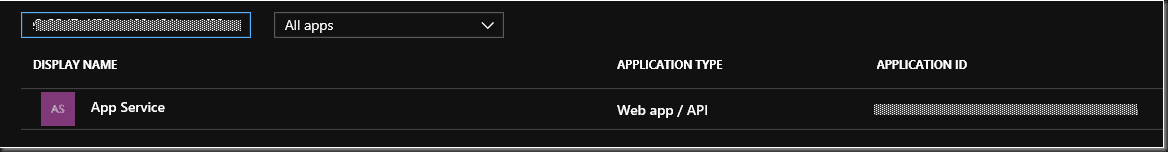
I filtered by the App ID.
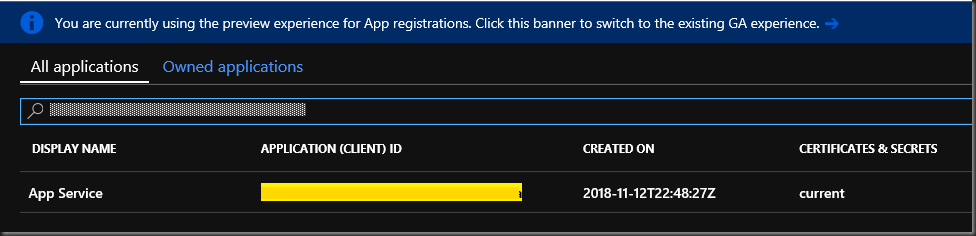
Filter by App ID
Click Settings

Settings
Select Required permissions and select Azure Stack
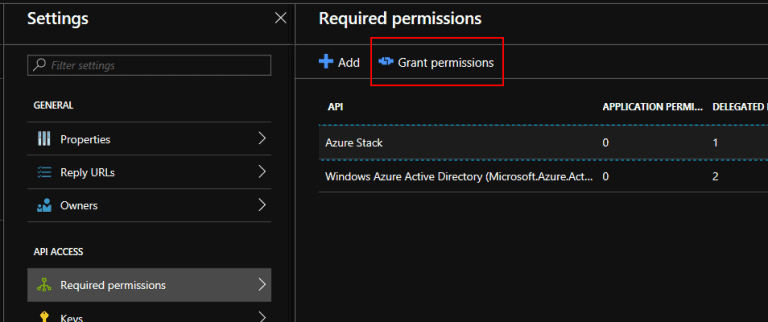
Grant permissions
Select Grant permissions and Yes
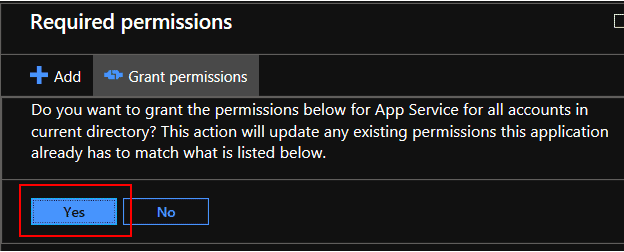
Required permissions
Done
Grant permissions
Great. You’re now ready to move on to the App Services installation process
3. Deploy HA File & SQL environment
The template: https://github.com/Azure/AzureStack-QuickStart-Templates/tree/master/appservice-fileserver-sqlserver-ha
Create a resource > Template deployment
Template deployment
Select > Edit Template
Edit template
On the github page for the template click the link to azuredeploy.json and view the raw text
Select all > copy
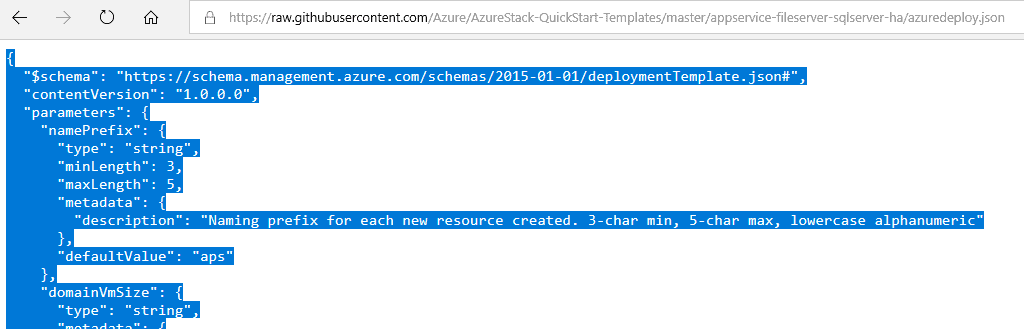
Copy all
Paste in the template replacing all existing text and click save
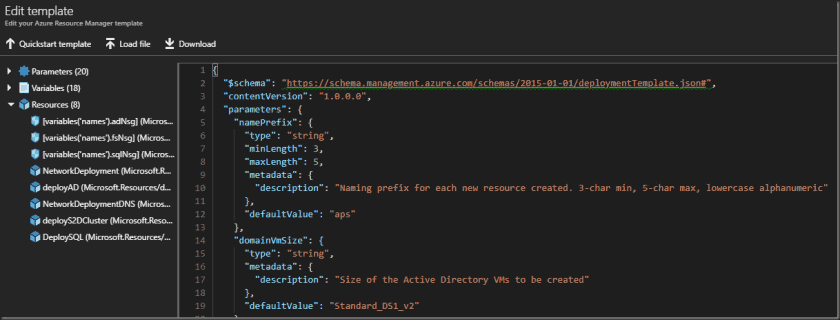
Edit template
Select Edit Parameters and modify to what suits you. Make sure you record down all changes including the passwords!
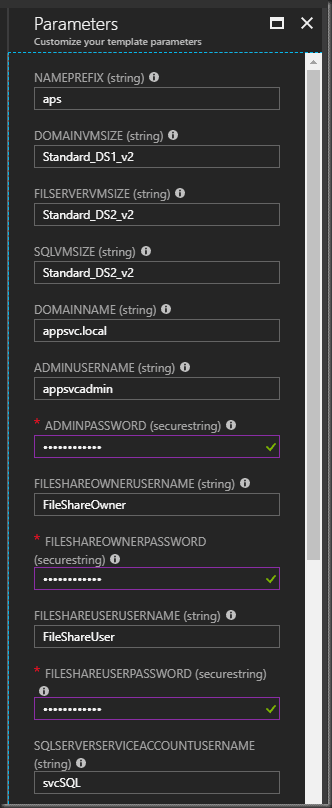
Parameters
Create the resources in the default provider subscription and I suggest creating a dedicated resource group
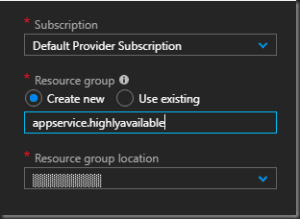
Subscription
Hit create and go find something else to do for an hour or so.
The template took about 1 hour and 12 minutes to deploy
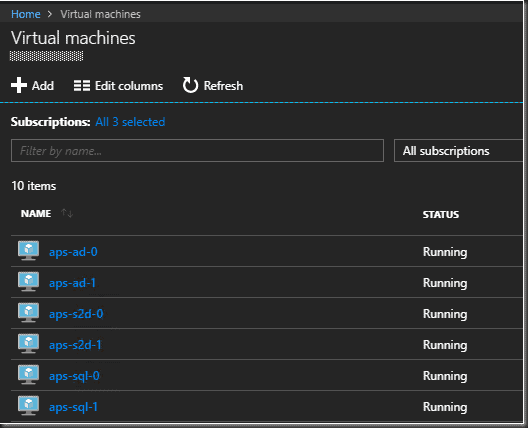
Virtual Machines
Check and save your outputs.
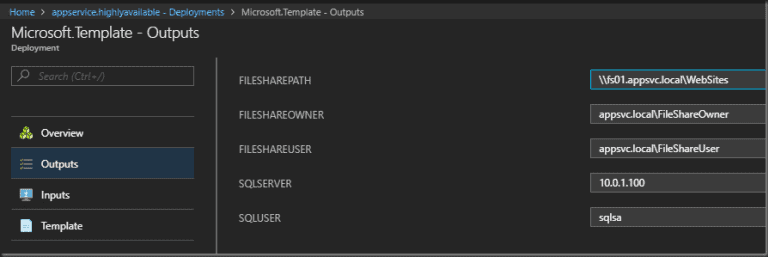
Microsoft Template – Outputs

First thing to do is create a group policy to disable automatic windows updates (I created a VM in the network that has all the pertinent management features).
4. Run the App Service 1.4 installer
Install App Services 1.4
Below is an abridged version of the install steps as we’ll skip the steps where we don’t need to make any modification
Microsoft Azure App Service 1.4
Next, Accept the Microsoft licence agreement
Next, Accept the 3rd party licence agreement
Enter your ARM endpoint URL. It should auto-populate the Tenant ARM and the Tenant Name
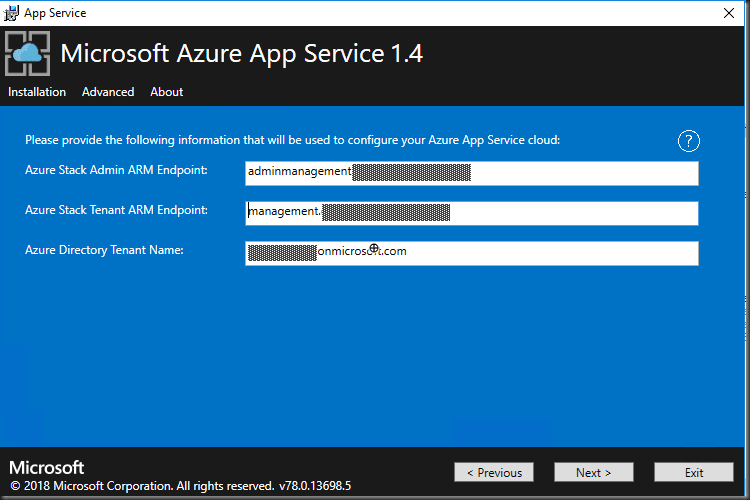
Microsoft Azure App Service 1.4
Next, click the Connect button and select the Default Provider Subscription and the Region
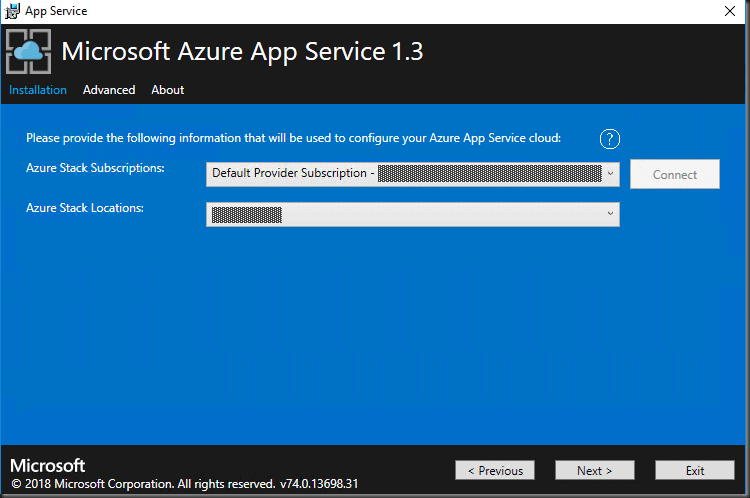
Microsoft Azure App Service 1.3
Because we deployed the HA template, choose use existing Virtual Network and Subnets and select the corresponding vnets and subnets as shown below
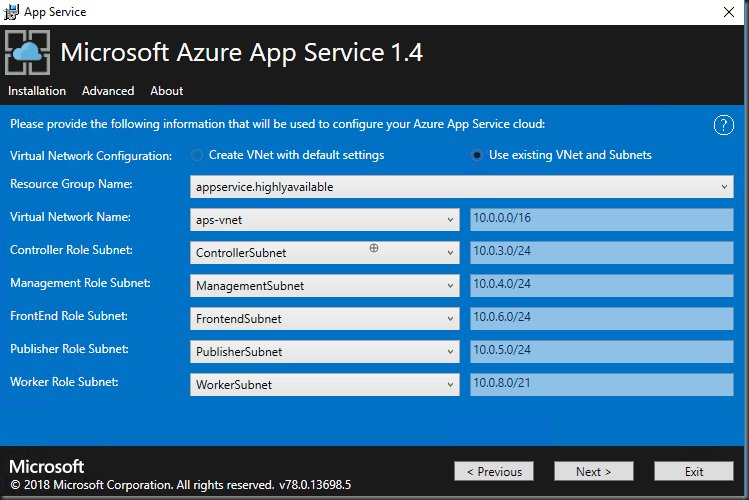
Microsoft Azure App Service 1.4
Enter the details provided by the Output from the ARM template deployment… You saved this right???
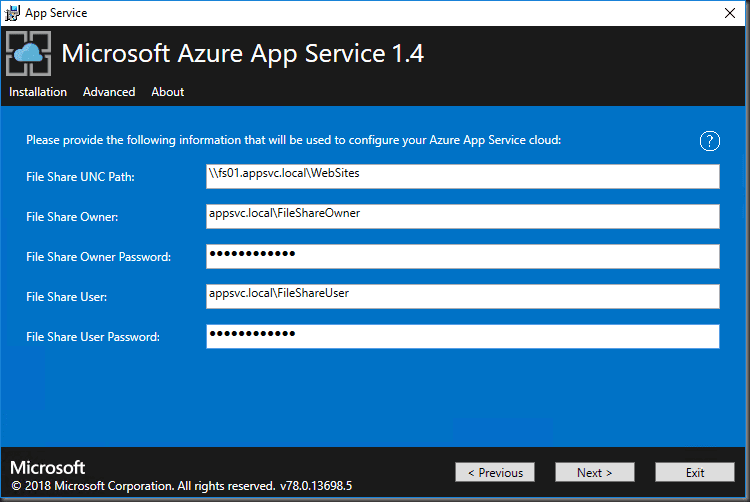
Microsoft Azure App Service 1.4
You will see the below error as the installer cannot verify access to the share.
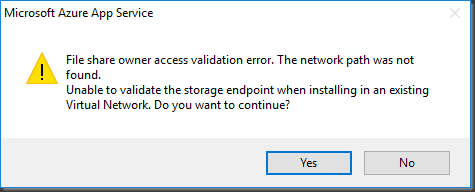
Microsoft Azure App Service
Enter the app ID details noted earlier.
Enter the SSO cert details and the path for the ARM root certificate exported in the earlier steps
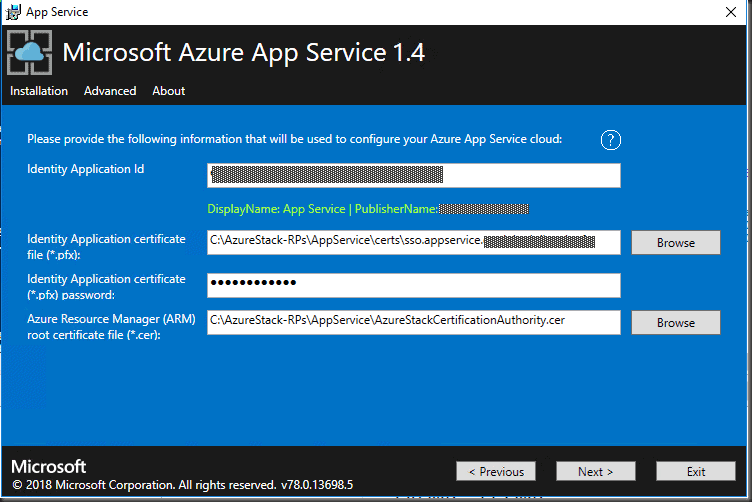
Microsoft Azure App Service 1.4
Same for the Domain, API and Publisher certs.
I suggest copy and paste the password as I have clumsy fingers 

Microsoft Azure App Service 1.4
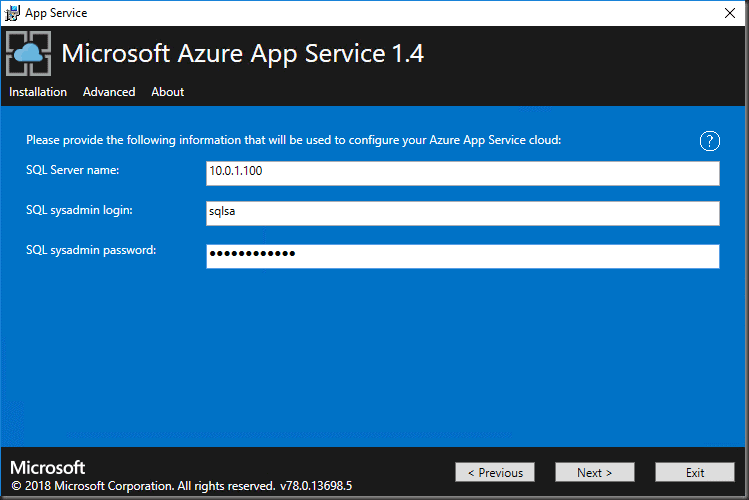
Microsoft Azure App Service 1.4
Enter the details of the SQL instance recorded earlier
Expect a similar error as the file share due to the installer being unable to validate the SQL details
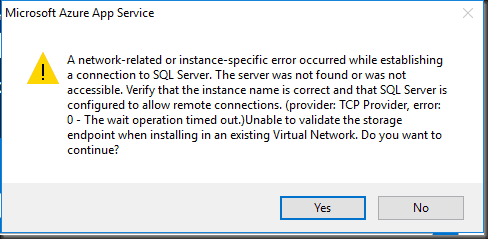
Microsoft Azure App Service
Based on the your sizing requirements, select the VM sizing that suits your deployment. These can be changed later so if unsure use the values provided below. These are the recommendations provided on the documentation.
I recommend at least a minimum of 2 instances for each role.
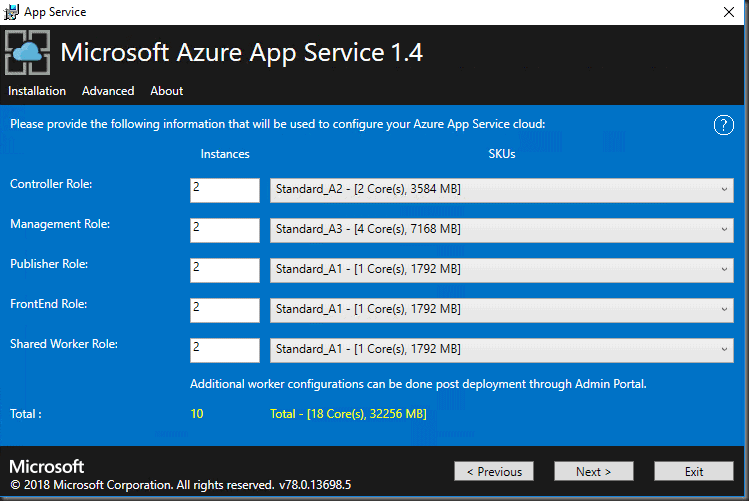
Microsoft Azure App Service 1.4
Select the Server 2016 image downloaded to the marketplace earlier
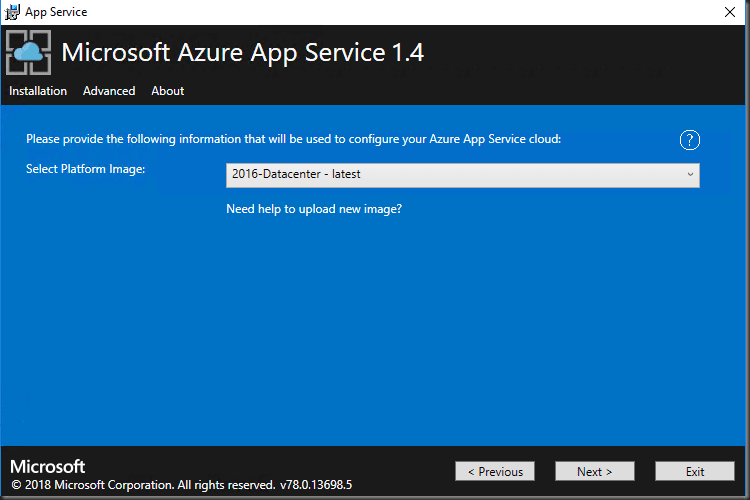
Microsoft Azure App Service 1.4
Enter in your preferred credentials. Again make sure you’re recording all of this somewhere safe.

Microsoft Azure App Service 1.4
Review your deployment configuration and export. Save the JSON file in the working folder.
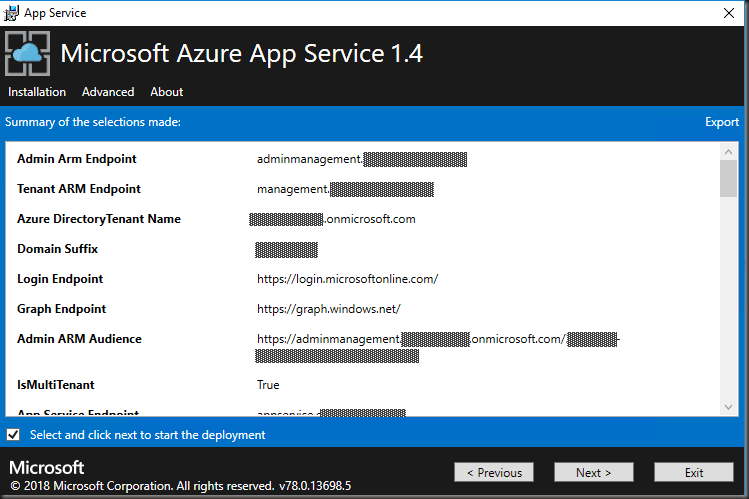
Microsoft Azure App Service 1.4
After reviewing, kick of the deployment.
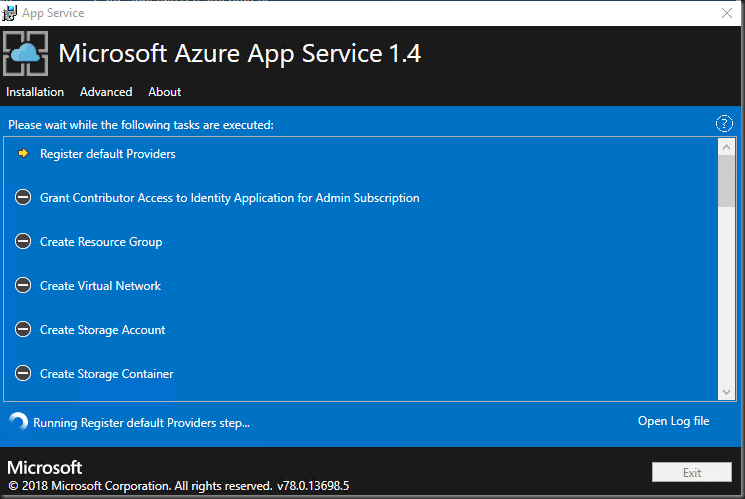
Microsoft Azure App Service 1.4
Open the log file and review
Those that know me will know I like to use cmtrace.exe
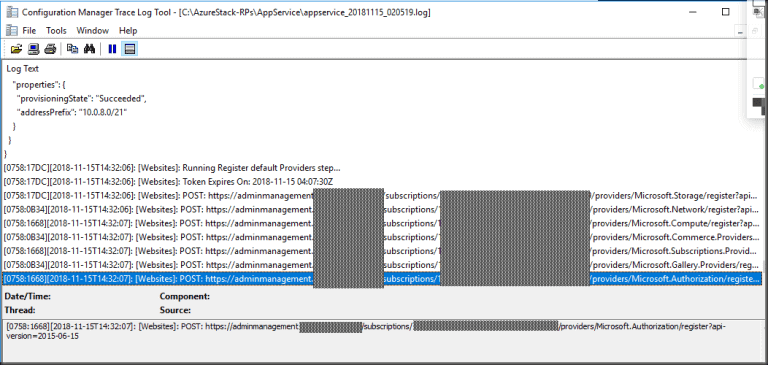
Configuration Manager
Go and do something else. Maybe read about quotas, plans and offers as you’ll need to understand this before your tenants will be able to subscribe

Microsoft Azure App Service 1.4
All things being equal you should come back to a successful deployment.
Note: my deployment took longer than expected. Total of about 2 hours.
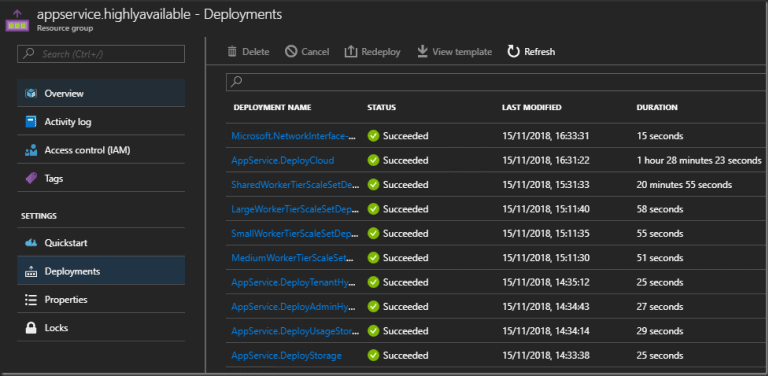
Deployments
Refresh the Admin Portal page in your browser
App Service
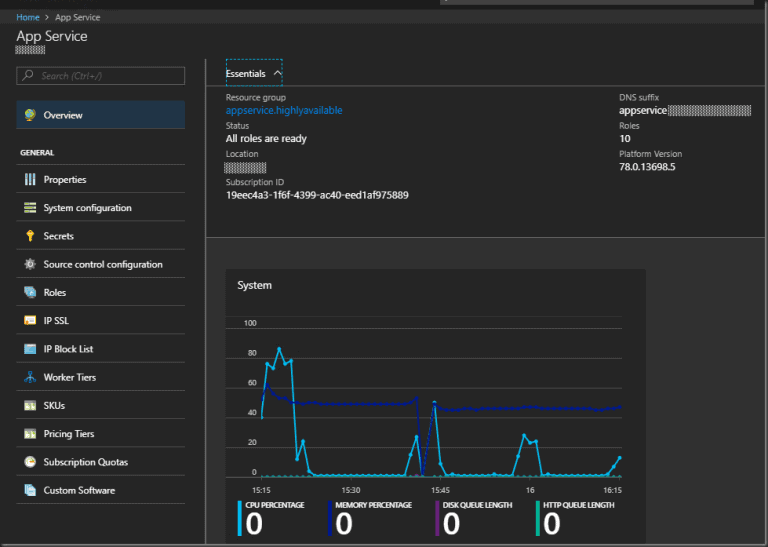
Open App Service blade to confirm it works… Not a doubt in my mind
App Service
Virtual Machines deployed (you won’t see aps-mgmt as I deployed this to do some post deploy config & testing)

Virtual Machines
Take a look at the Virtual Machine Scale Sets deployed.
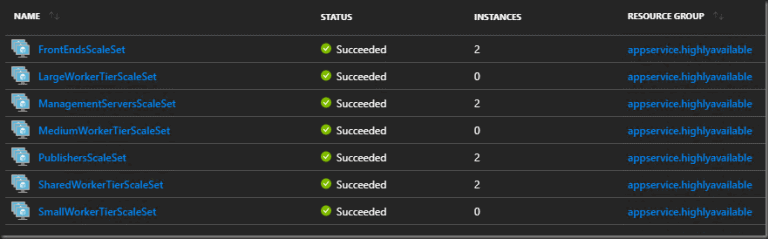
Virtual Machine Scale Sets
Last part of the deployment process requires the Web Worker NSG to be updated to allow the Workers to connect to our file server via SMB
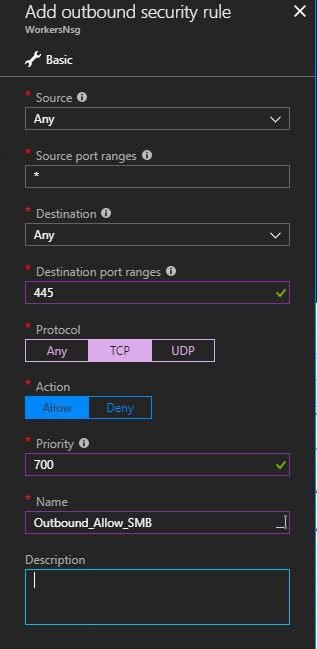
Add outbound security role
Select Create a resource > Web + Mobile and see your new available app services
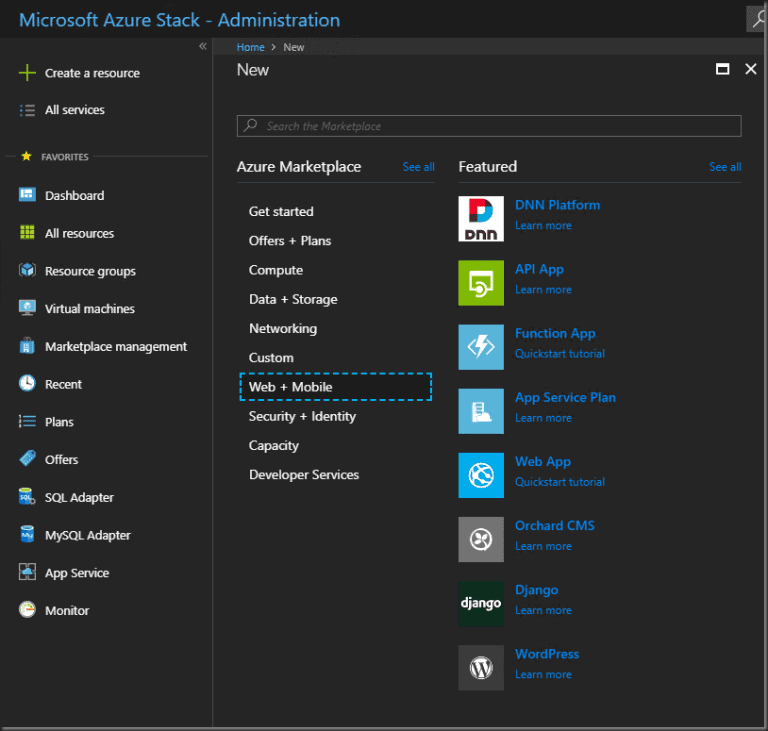
Web and mobile
Create a web service and once complete, browse to the URL
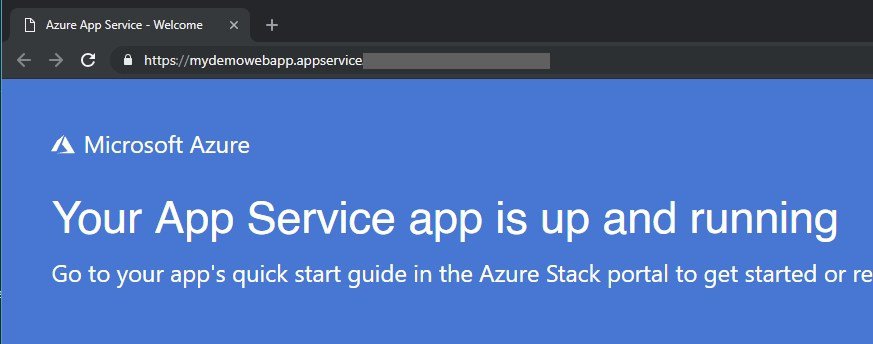
App up and running
Congratulations! You’ve successfully installed a HA App Service resource provider on your Azure Stack Integrated System
Next is the post-deployment configuration.
Highly Available App Service 1.4 on Azure Stack – Step 3: Post-deployment setup (in progress)
See you in the next post
Happy stacking!
Dan
About the Author:
My name is Daniel Apps and I have been working in the IT industry since 1999. I am a Solutions Architect at Vigilant.IT and also a Microsoft P-TSP (Technology Solutions Professional).
I’m based in beautiful Sydney, Australia and have worked at Vigilant.IT since 2009. The count down to long service leave has begun!
My tech interests are currently focused around the Software Defined Datacenter (SDDC) with Windows Server and System Center however my consulting projects typically encompass most common MS technologies.
My recent Microsoft certifications are:
- MCSE: Cloud Platform and Infrastructure
- MCSA: Windows Server 2016
Check out my Twitter for more: @daniel_apps
Reference:
Apps, D. (2018). Adventures of a Cloud Operator: Highly Available App Service 1.4 on Azure Stack – Step 2: Deployment. Avilable at: http://blog.apps.id.au/adventures-cloud-operator-highly-available-app-service-1-4-azure-stack-step-2-deployment/ [Accessed 25th January 2019]








 Using a SharePoint Online list as a Knowledge source via ACTIONS in Copilot AI Studio
Using a SharePoint Online list as a Knowledge source via ACTIONS in Copilot AI Studio
