Hi All,
A few Years ago i wrote an Article on how to Grant Access to a Entra App in Sharepoint to upload Files to a SharePoint Site with PnP.PowerShell
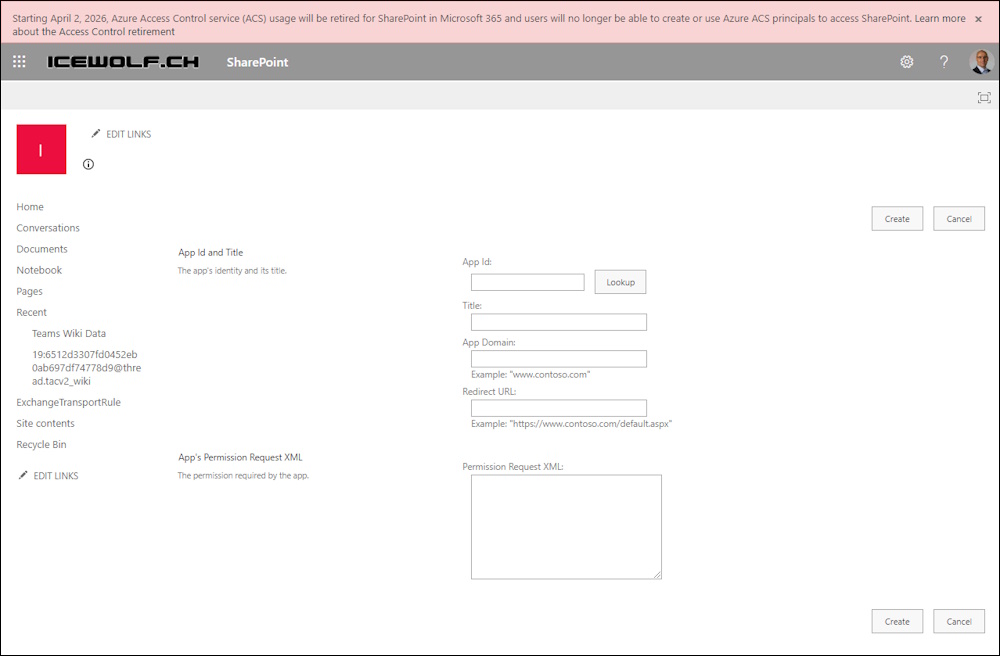
I wanted to do the same thing and there is a big red bar on top, that informs about the Azure ACS Retirement in April 2026.
Starting April 2, 2026, Azure Access Control service (ACS) usage will be retired for SharePoint in Microsoft 365 and users will no longer be able to create or use Azure ACS principals to access SharePoint. Learn more about the Access Control retirement
You can still add Permissions to SharePoint
https://[tenant].sharepoint.com/sites/[siteName]/_layouts/appinv.aspx
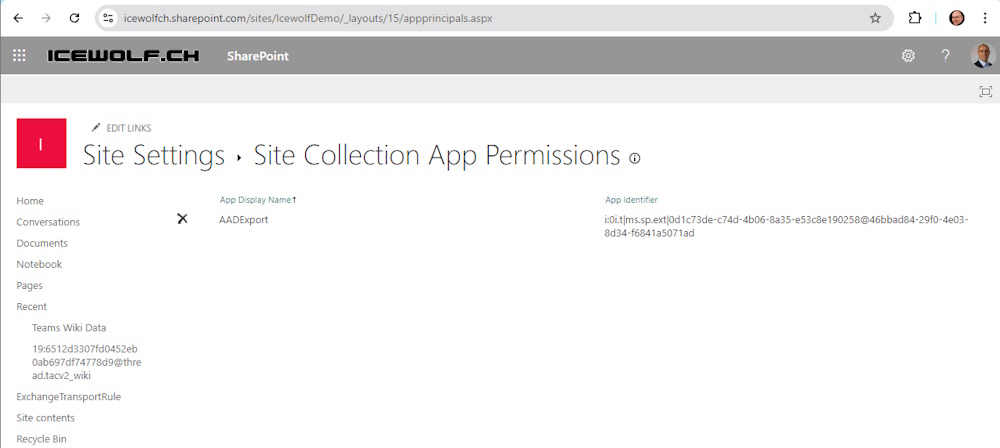
And review them here
- Azure ACS retirement in Microsoft 365 Azure ACS will stop working for new tenants as of November 1st, 2024 and it will stop working for existing tenants and will be fully retired as of April 2nd, 2026.
- SharePoint Add-In retirement in Microsoft 365 SharePoint Add-Ins will stop working for new tenants as of November 1st, 2024 and they will stop working for existing tenants and will be fully retired as of April 2nd, 2026
Assessment
They recommend to run the Microsoft 365 Assessment tool
I’ve created an Entra ID Application with the required Permissions
Application
- Graph: Sites.Read.All
- Graph: Application.Read.All
- SharePoint: Sites.Read.All
Delegated
- Graph: Sites.Read.All
- Graph: Application.Read.All
- Graph: User.Read
- SharePoint: AllSites.Read
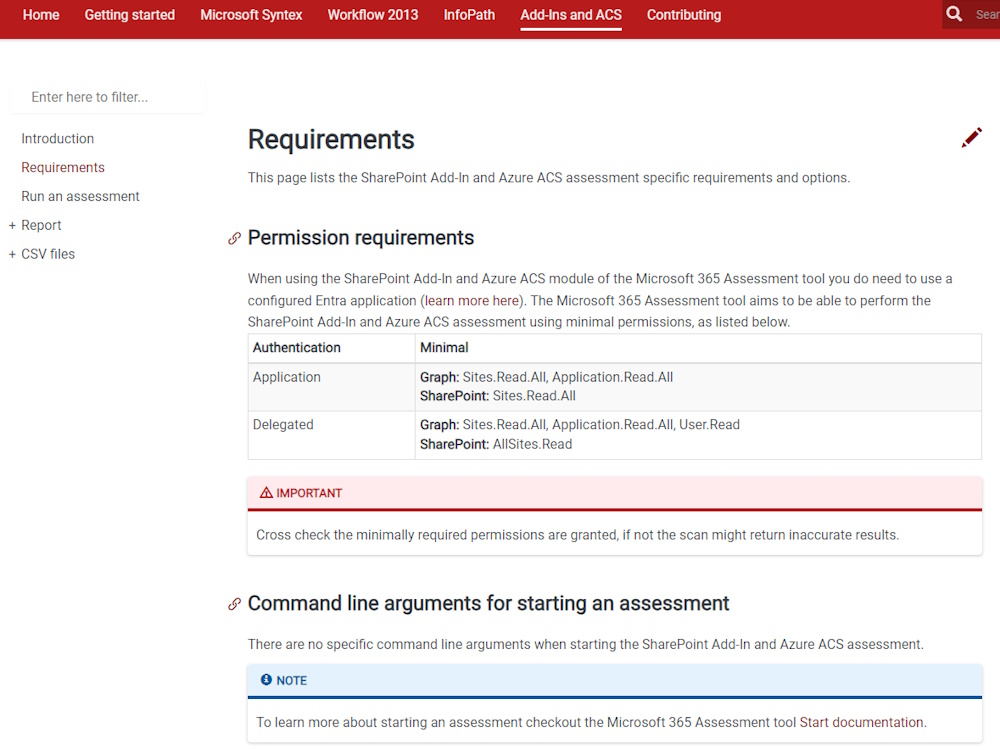
The SharePoint Permissions are a little bit tricky, you need to select “API’s my organization uses” and then search for “Office 365 SharePoint Online”
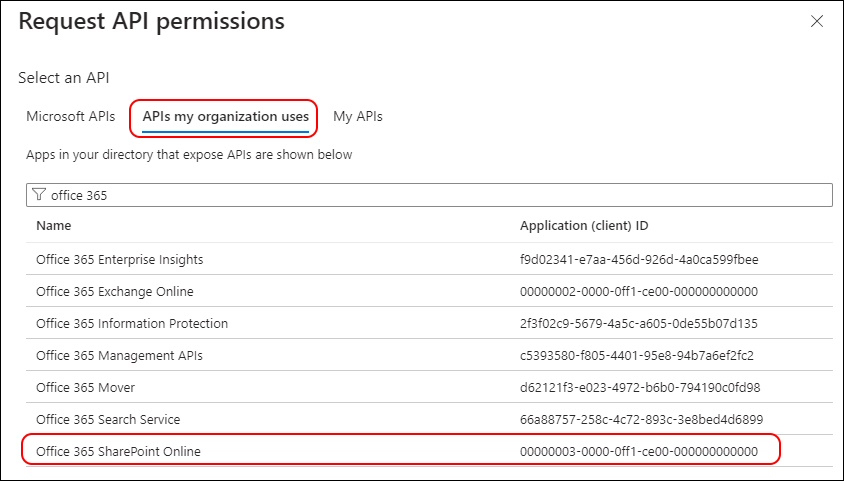
Now you can select the Permission
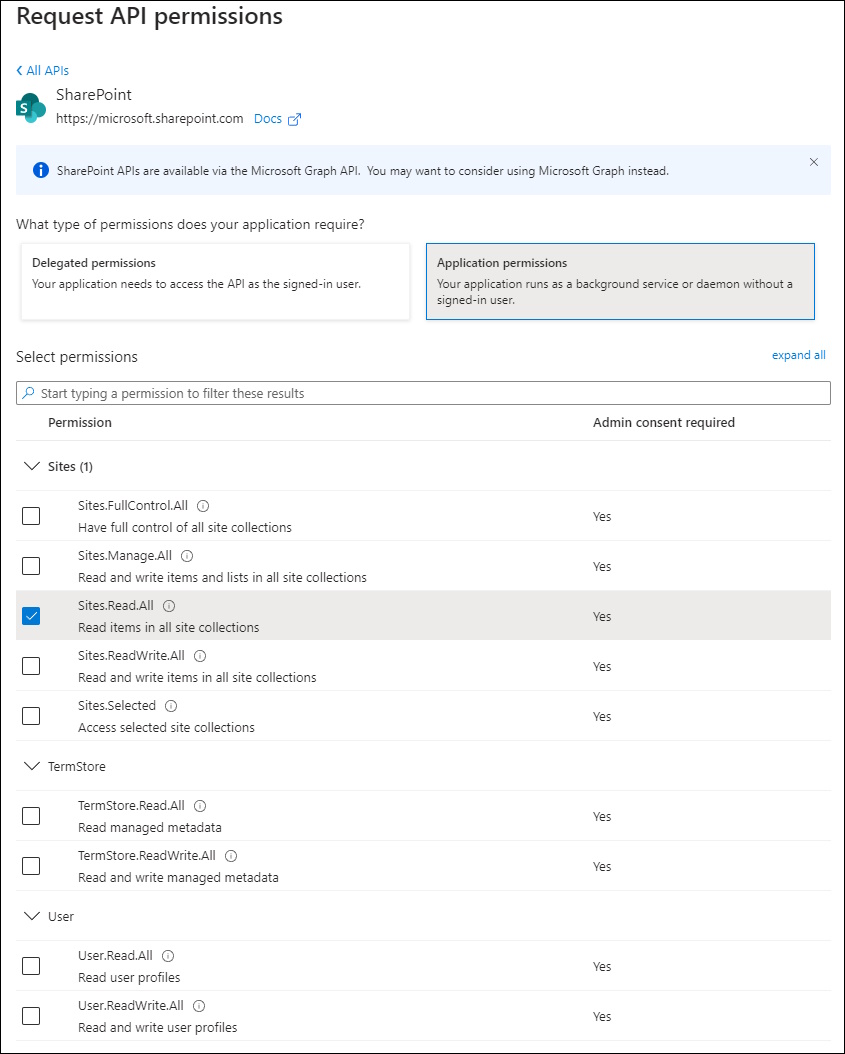
I’ve used Application Permission and granted Admin Consent
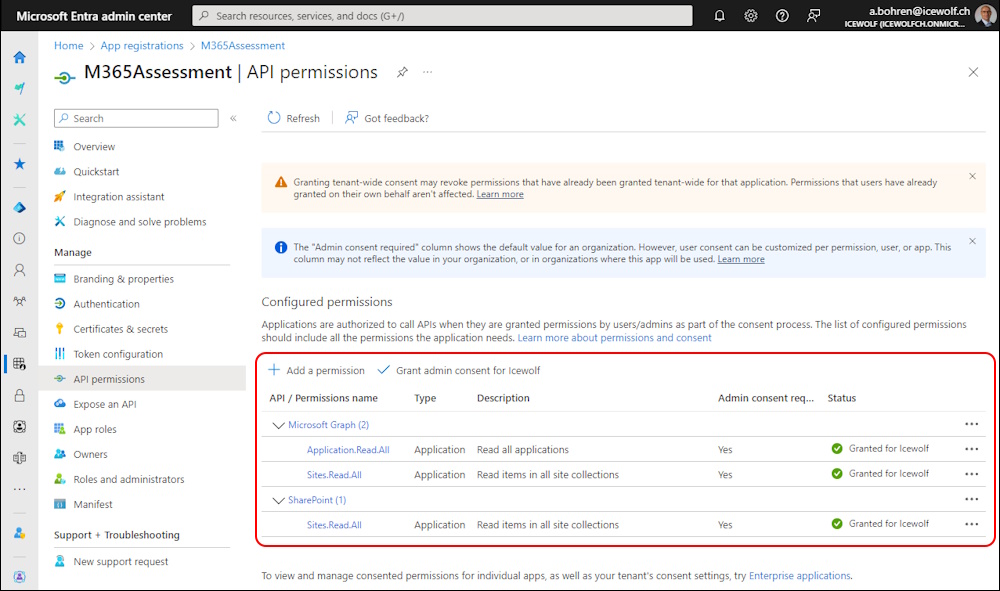
Using a Certificate for Authentication
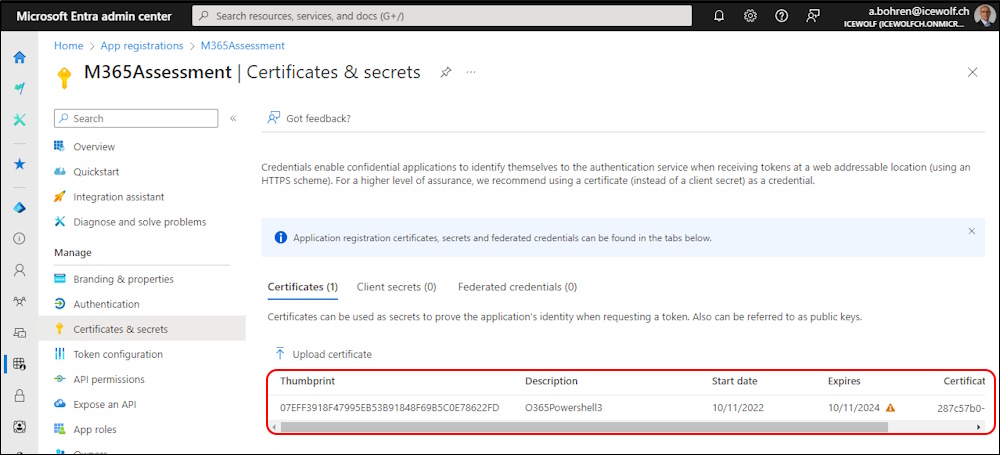
Starting Assessment
Now i am able to start the Assessment with the M365 Assessment Tool
microsoft365-assessment.exe start --mode AddInsACS --authmode application --tenant icewolfch.sharepoint.com --applicationid 52b87847-5a39-42b1-9119-790a6c275069 --certpath "My|CurrentUser|07EFF3918F47995EB53B91848F69B5C0E78622FD"
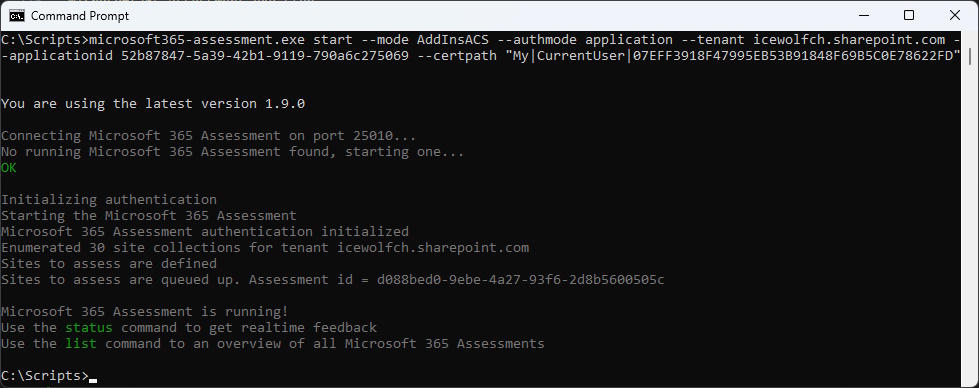
Now there are a bunch of Commands that you can use
microsoft365-assessment.exe status
microsoft365-assessment.exe list
microsoft365-assessment.exe stop
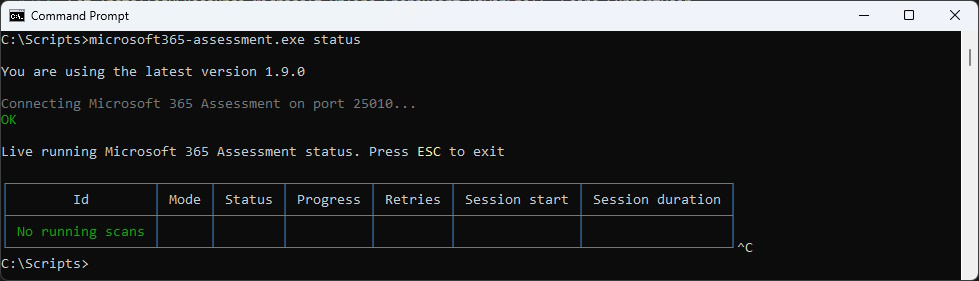
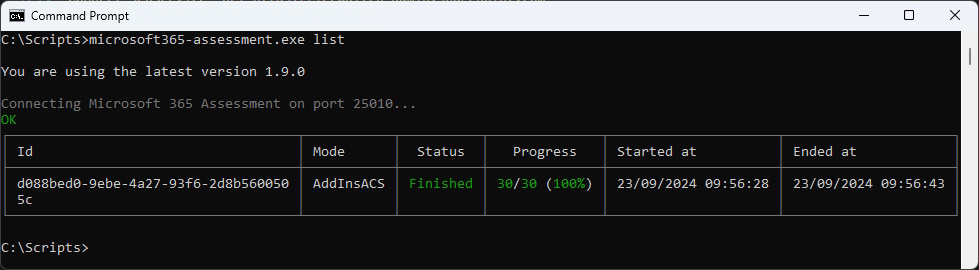
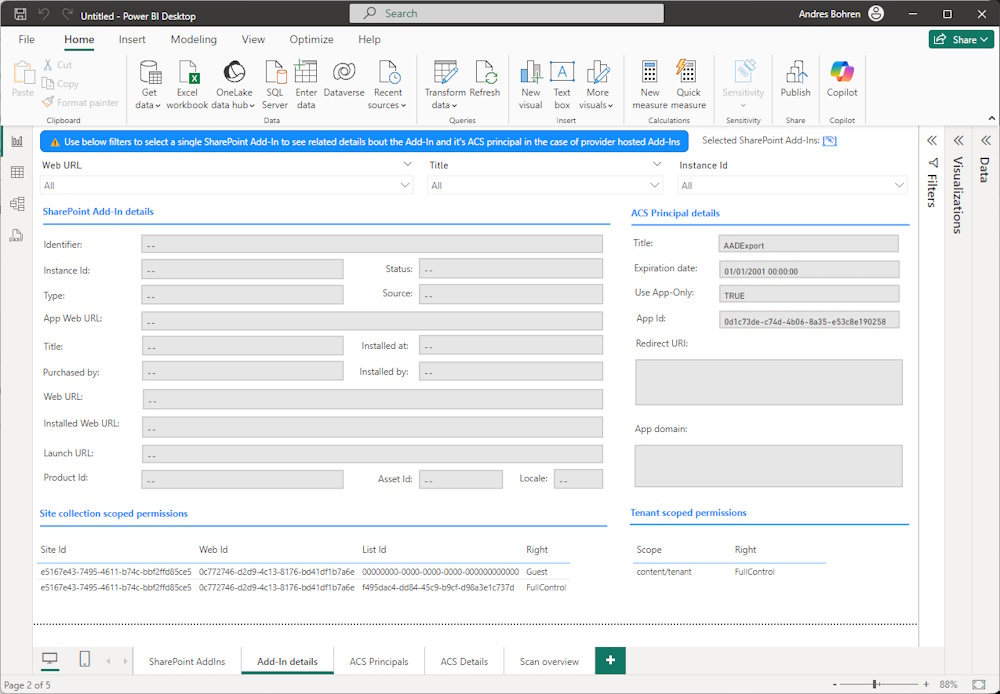
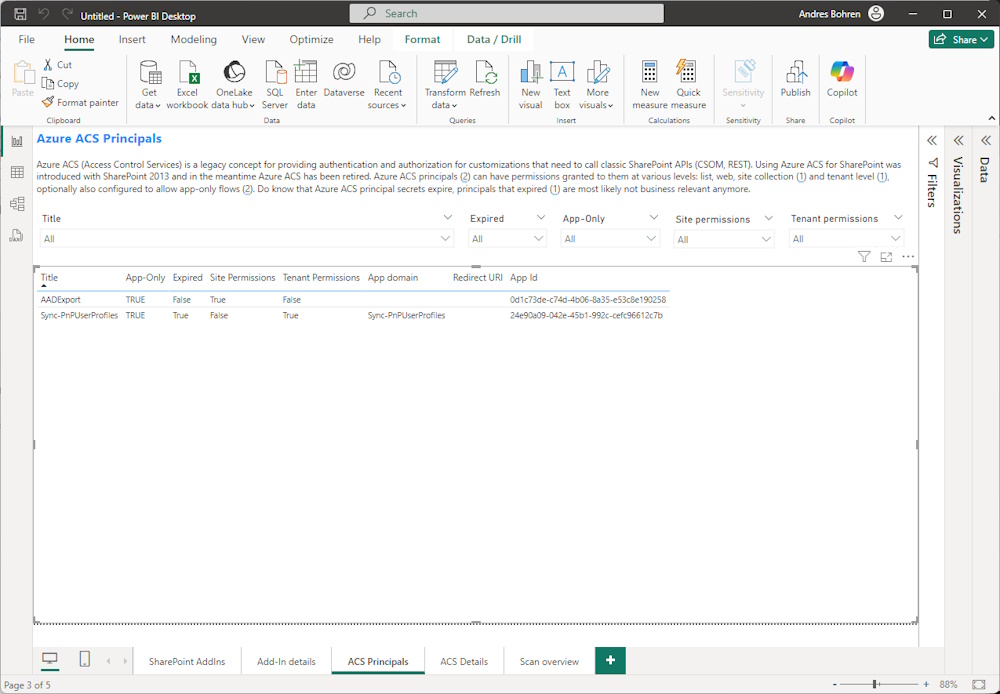
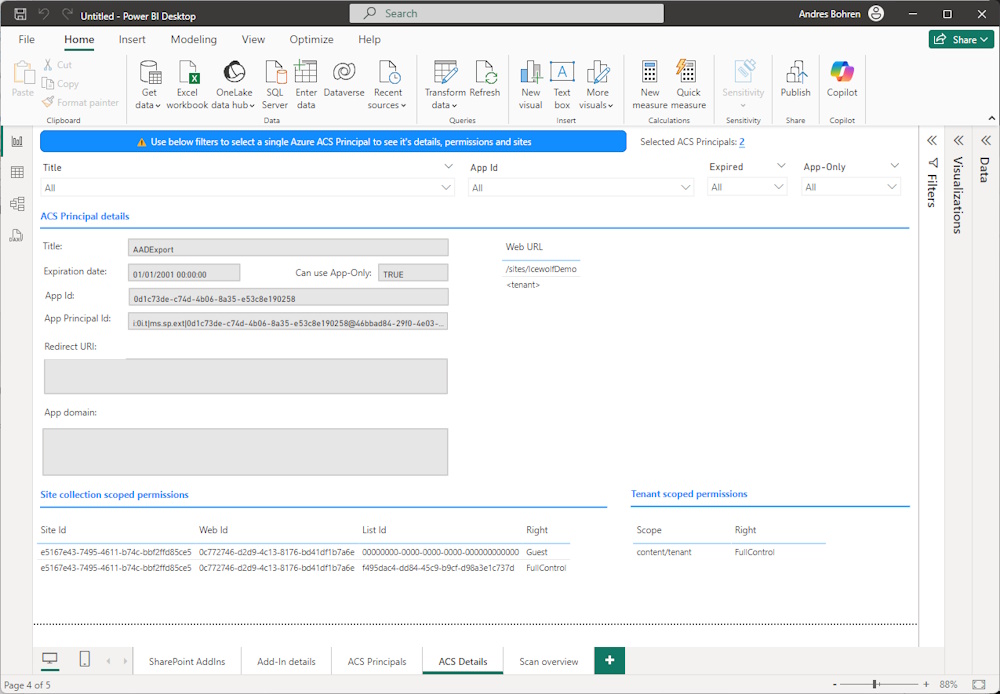
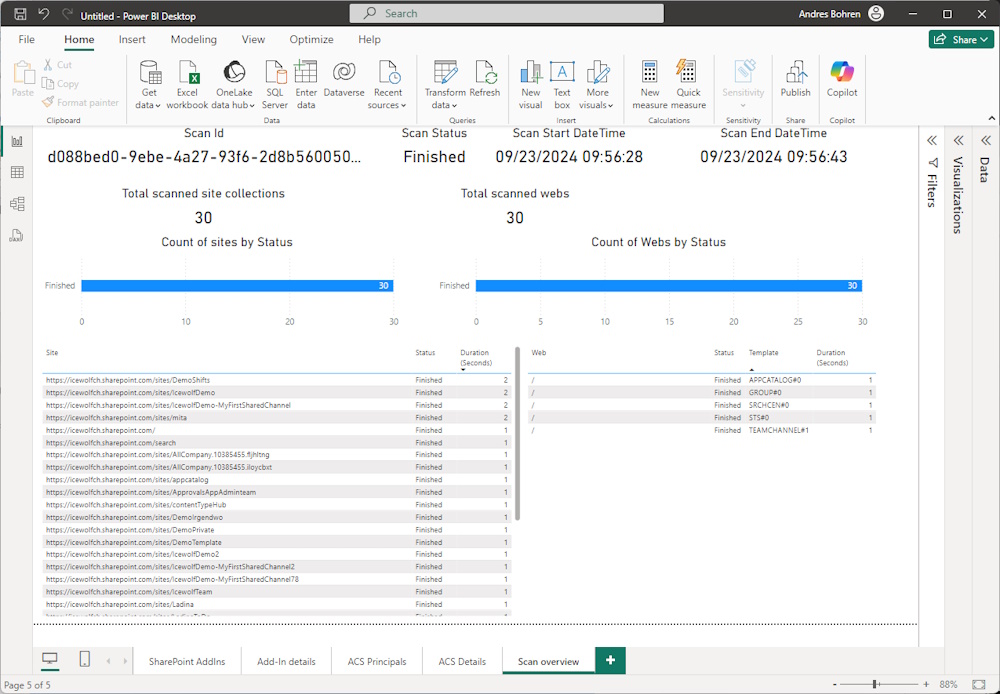
Report
With the ID of the Scan you can Export CSV Files
microsoft365-assessment.exe report --id d088bed0-9ebe-4a27-93f6-2d8b5600505c --mode CsvOnly --path "c:\Scripts\reports"
You will get a bunch of CSV Files
microsoft365-assessment.exe report --id d088bed0-9ebe-4a27-93f6-2d8b5600505c
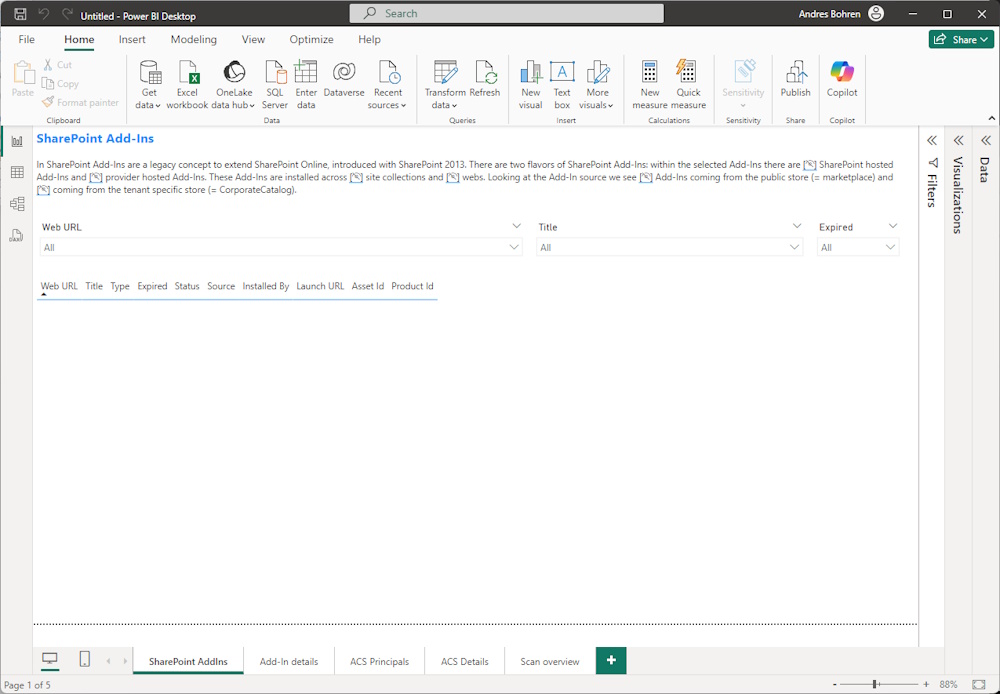
Changes
Testing current Access
Testing current Access
###############################################################################
# Upload file to SharePoint with PnP.PowerShell
# 23.01.2022 - Andres Bohren
###############################################################################
#Variables
$AppID = "0d1c73de-c74d-4b06-8a35-e53c8e190258" #AADUsers
$ClientSecret = "YourClientSecret"
$SiteURL = "https://icewolfch.sharepoint.com/sites/IcewolfDemo/"
$FileURL = "Freigegebene Dokumente/AADExport/AADUsers.csv"
#Connect-PnPOnline
Write-Output "Connect-PnPOnline"
Connect-PnPOnline -Url $SiteURL -ClientId $AppID -ClientSecret $ClientSecret -WarningAction Ignore
#Get-PnPContext
#Items in Folder
$RelativeURL = "Freigegebene Dokumente/AADExport"
$Items = Get-PnPFolderItem -FolderSiteRelativeUrl $RelativeURL
$Items
#Upload File
$CSVFile = "C:\GIT_WorkingDir\PowerShellScripts\SharePoint\AADUsers.csv"
Write-Output "Uploading CSV to Sharepoint"
$FolderObject = Get-PnPFolder -Url $RelativeURL
$Upload = Add-PnPFile -Path $CSVFile -Folder $FolderObject
If ($Upload -ne $null)
{
Write-Output "File sucessfully uploaded"
}
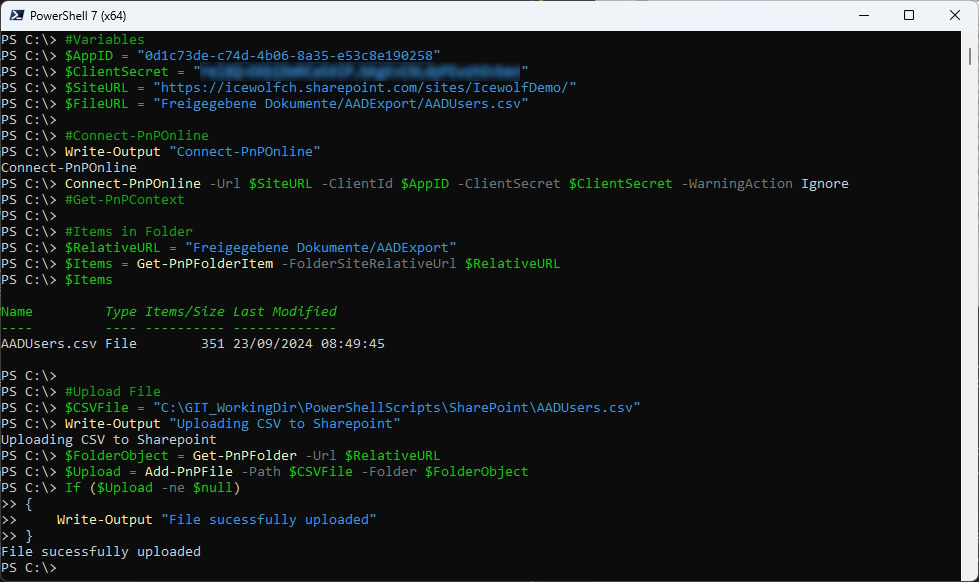
Remove Application
Remove the Application Access from Sharepoint
https://[tenant].sharepoint.com/sites/[siteName]/_layouts/15/appprincipals.aspx
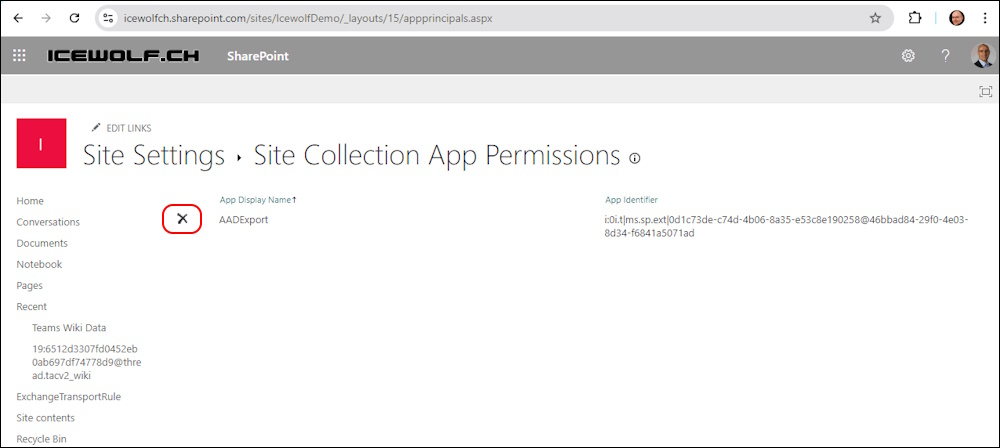
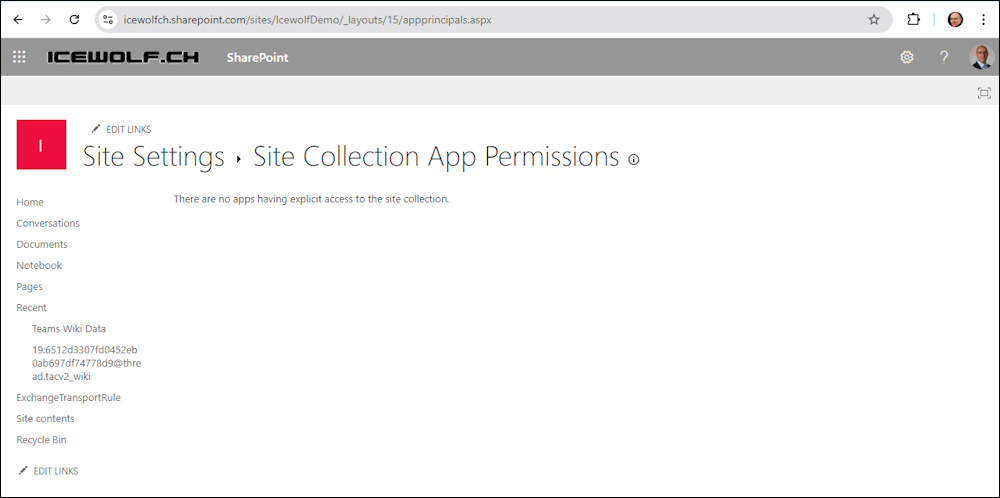
Testing after the Application has been removed
#Variables
$AppID = "0d1c73de-c74d-4b06-8a35-e53c8e190258"
$ClientSecret = "YourClientSecret"
$SiteURL = "https://icewolfch.sharepoint.com/sites/IcewolfDemo/"
$FileURL = "Freigegebene Dokumente/AADExport/AADUsers.csv"
#Connect-PnPOnline
Write-Output "Connect-PnPOnline"
Connect-PnPOnline -Url $SiteURL -ClientId $AppID -ClientSecret $ClientSecret -WarningAction Ignore
#Get-PnPContext
#Items in Folder
$RelativeURL = "Freigegebene Dokumente/AADExport"
$Items = Get-PnPFolderItem -FolderSiteRelativeUrl $RelativeURL
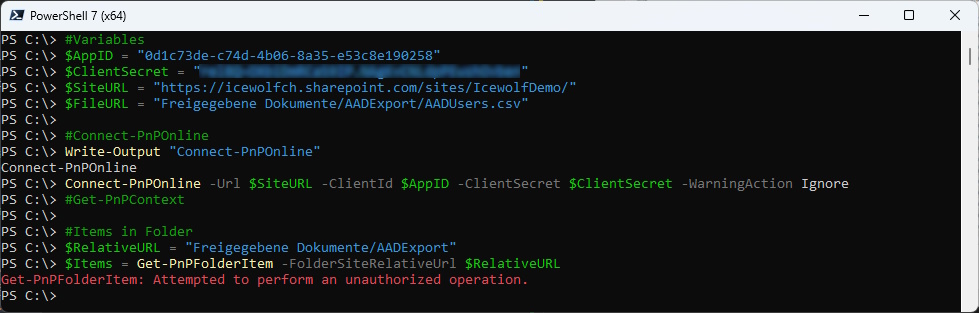
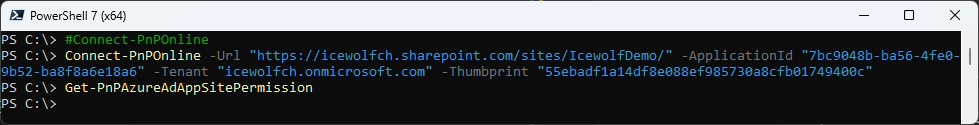
Get-PnPAzureAdAppSitePermission
Now we check the Permission with Get-PnPAzureAdAppSitePermission. As you can see there are no Permissions.
Logged in with the New Entra ID App for Sharepoint Register-PnPEntraIDApp
#Connect-PnPOnline with SharePoint App (Sharepint Administrator)
Connect-PnPOnline -Url "https://icewolfch.sharepoint.com/sites/IcewolfDemo/" -ApplicationId "7bc9048b-ba56-4fe0-9b52-ba8f8a6e18a6" -Tenant "icewolfch.onmicrosoft.com" -Thumbprint "55ebadf1a14df8e088ef985730a8cfb01749400c"
#Get Permission
Get-PnPContext
Get-PnPAzureAdAppSitePermission
Get-PnPAzureADAppSitePermission -AppIdentity "0d1c73de-c74d-4b06-8a35-e53c8e190258" #AADExport
Get-PnPAzureADAppSitePermission -Site "https://icewolfch.sharepoint.com/sites/DemoTemplate"
Grant-PnPAzureADAppSitePermission
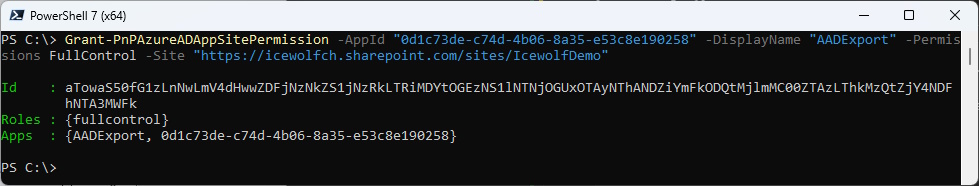
Now we add the Permission to the SharePoint Site with PnP.Powershell Grant-PnPAzureADAppSitePermission
#Grant Permission
Grant-PnPAzureADAppSitePermission -AppId "0d1c73de-c74d-4b06-8a35-e53c8e190258" -DisplayName "AADExport" -Permissions FullControl -Site "https://icewolfch.sharepoint.com/sites/IcewolfDemo"
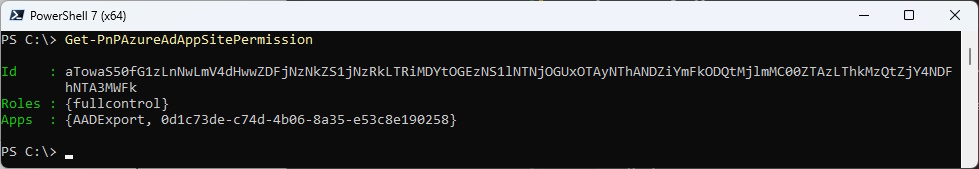
If we check the AppPermission now, we can see an entry
Get-PnPAzureAdAppSitePermission
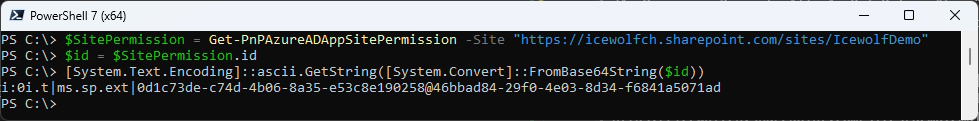
By the way, the ID is Base64 Encoded and can be Decoded with the following PowerShell code
$SitePermission = Get-PnPAzureADAppSitePermission -Site "https://icewolfch.sharepoint.com/sites/IcewolfDemo"
$id = $SitePermission.id
[System.Text.Encoding]::ascii.GetString([System.Convert]::FromBase64String($id))
Checking if the Code works again
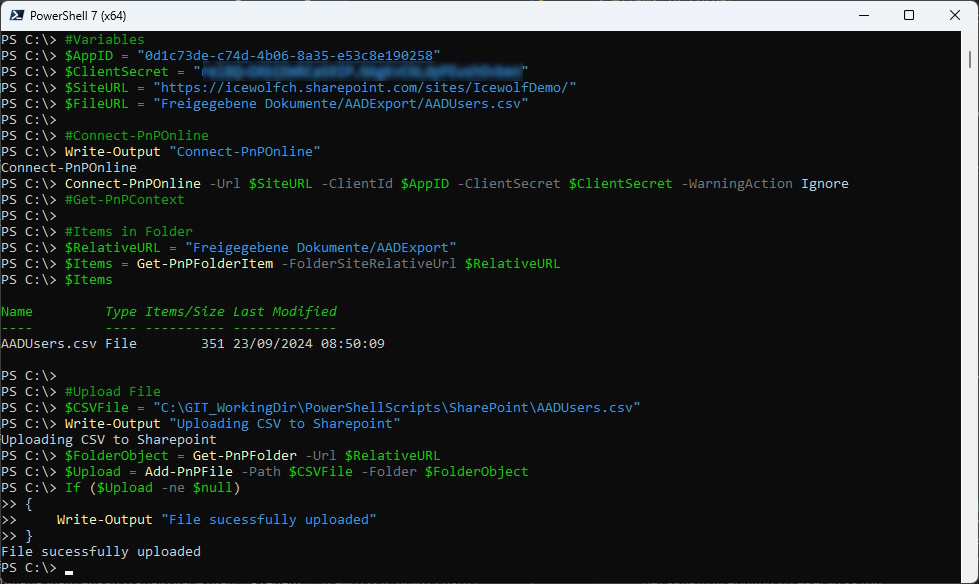
#Variables
$AppID = "0d1c73de-c74d-4b06-8a35-e53c8e190258" #AADUsers
$ClientSecret = "YourClientSecret"
$SiteURL = "https://icewolfch.sharepoint.com/sites/IcewolfDemo/"
$FileURL = "Freigegebene Dokumente/AADExport/AADUsers.csv"
#Connect-PnPOnline
Write-Output "Connect-PnPOnline"
Connect-PnPOnline -Url $SiteURL -ClientId $AppID -ClientSecret $ClientSecret -WarningAction Ignore
#Get-PnPContext
#Items in Folder
$RelativeURL = "Freigegebene Dokumente/AADExport"
$Items = Get-PnPFolderItem -FolderSiteRelativeUrl $RelativeURL
$Items
#Upload File
$CSVFile = "C:\GIT_WorkingDir\PowerShellScripts\SharePoint\AADUsers.csv"
Write-Output "Uploading CSV to Sharepoint"
$FolderObject = Get-PnPFolder -Url $RelativeURL
$Upload = Add-PnPFile -Path $CSVFile -Folder $FolderObject
If ($Upload -ne $null)
{
Write-Output "File sucessfully uploaded"
}
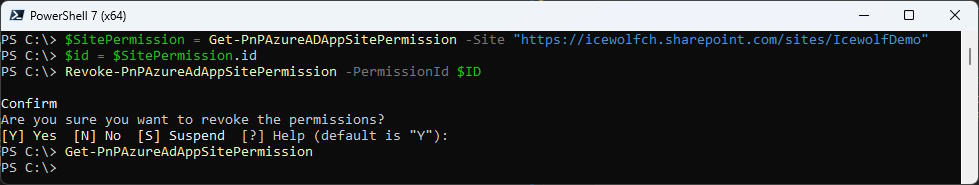
Remove Permission
Just to be complete, i’ve added here the Code how to remove the Permission for an Entra App from a SharePoint Site
#Remove Permission
$SitePermission = Get-PnPAzureADAppSitePermission -Site "https://icewolfch.sharepoint.com/sites/IcewolfDemo"
$id = $SitePermission.id
Revoke-PnPAzureAdAppSitePermission -PermissionId $ID
Get-PnPAzureAdAppSitePermission
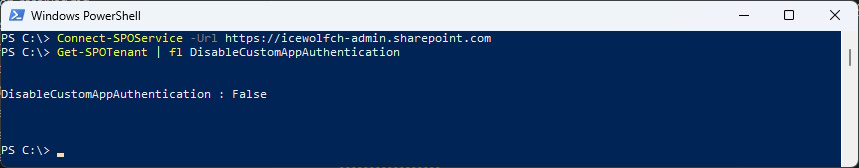
Disable Azure ACS
When all Applications have been migrated you can Activate the SharePoint Tenant Parameter “DisableCustomAppAuthentication”
PowerShell 5
Connect-SPOService -Url https://icewolfch-admin.sharepoint.com
Get-SPOTenant | fl DisableCustomAppAuthentication
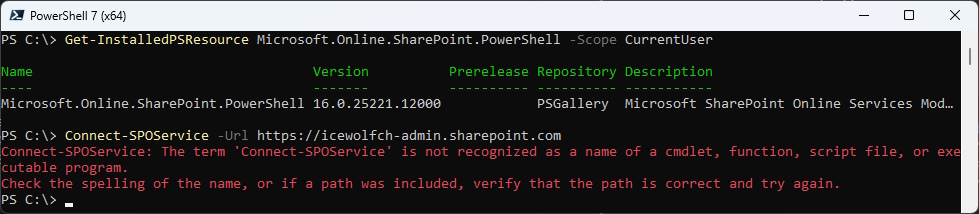
PowerShell 7 gives us an error – even the Module is installed
Get-InstalledPSResource Microsoft.Online.SharePoint.PowerShell -Scope CurrentUser
Connect-SPOService -Url https://icewolfch-admin.sharepoint.com
You need to Import the Module in PowerShell 7 as PowerShell 5 Module
Import-Module Microsoft.Online.SharePoint.PowerShell -UseWindowsPowerShell -WarningAction SilentlyContinue
Connect-SPOService -Url https://icewolfch-admin.sharepoint.com
Get-SPOTenant | fl DisableCustomAppAuthentication
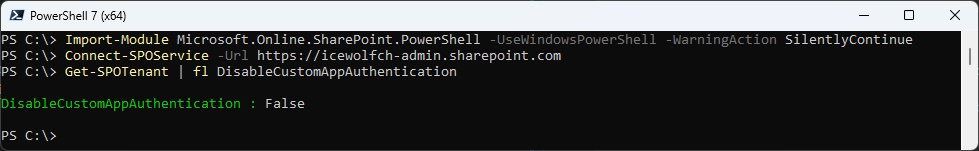
DisableCustomAppAuthentication
Set-SPOTenant -DisableCustomAppAuthentication $true
Get-SPOTenant | fl DisableCustomAppAuthentication
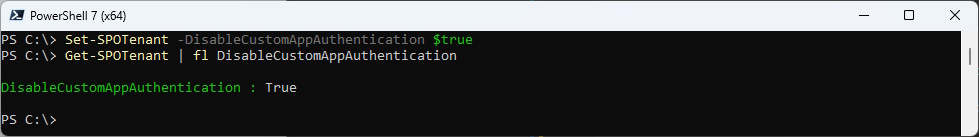
Adoption
After the DisableCustomAppAuthentication the Script get’s a 401 Unauthorized Error.
#Variables
$AppID = "0d1c73de-c74d-4b06-8a35-e53c8e190258"
$ClientSecret = "YourClientSecret"
$SiteURL = "https://icewolfch.sharepoint.com/sites/IcewolfDemo/"
$FileURL = "Freigegebene Dokumente/AADExport/AADUsers.csv"
#Connect-PnPOnline
Write-Output "Connect-PnPOnline"
Connect-PnPOnline -Url $SiteURL -ClientId $AppID -ClientSecret $ClientSecret -WarningAction Ignore
#Get-PnPContext
#Items in Folder
$RelativeURL = "Freigegebene Dokumente/AADExport"
$Items = Get-PnPFolderItem -FolderSiteRelativeUrl $RelativeURL
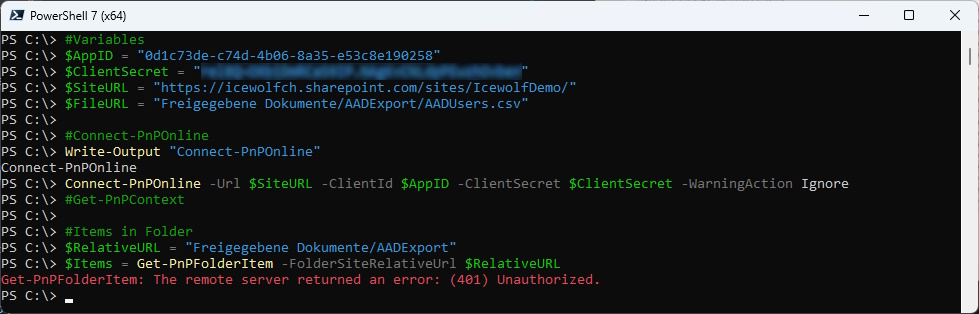
The Entra Application has to be extended with the two Permissions:
- Sharepoint: Sites.Selected
- Graph: Sites.Selected
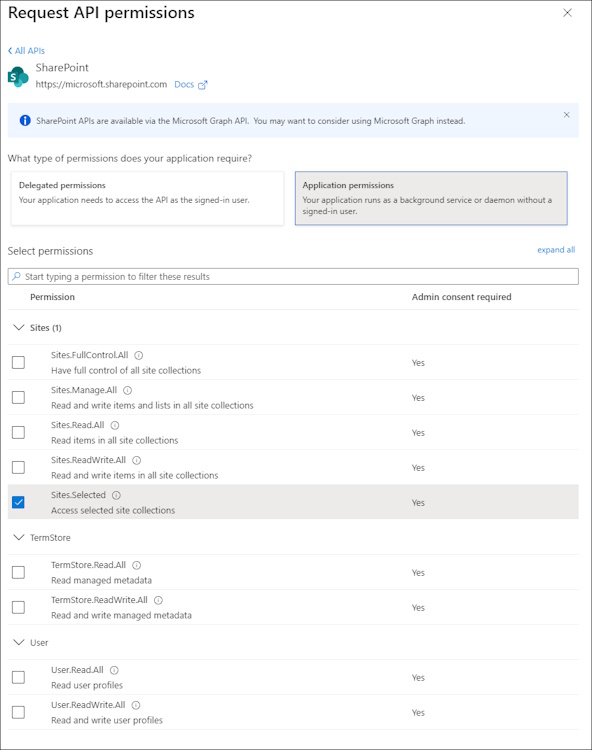
Then you need to Grant Admin Consent
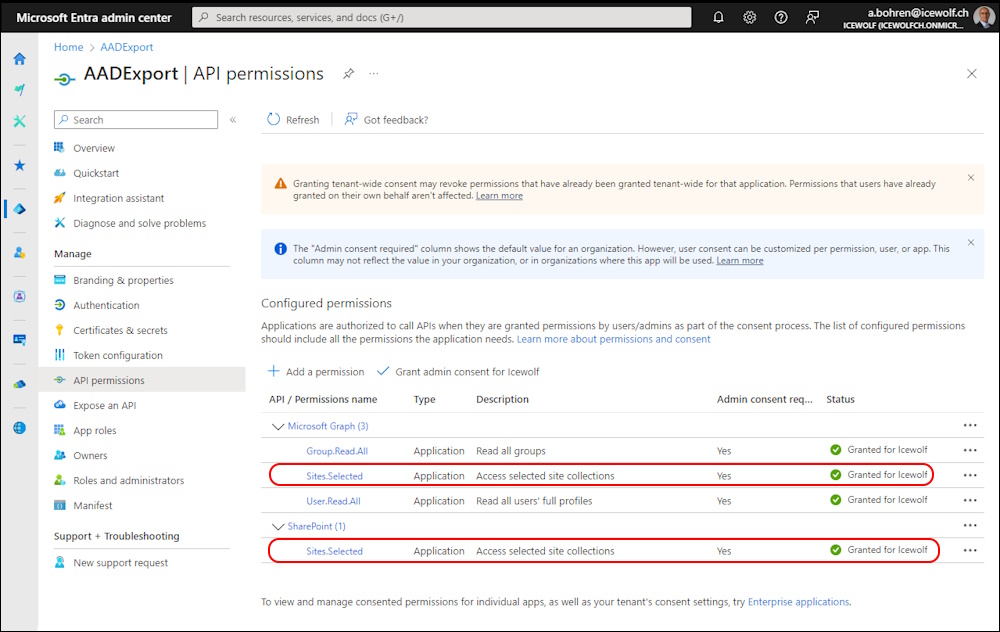
On the Application i needed to switch from ClientSecret to Certificate and add the Tenant Parameter
Connect-PnPOnline -Url <SharePointSiteURL> -ClientId <AzureAppID> -Thumbprint <CertThumbprint> -Tenant "<Tenant>.onmicrosoft.com"
###############################################################################
# Upload file to SharePoint with PnP.PowerShell
# 23.01.2022 - Andres Bohren
###############################################################################
#Variables
$AppID = "0d1c73de-c74d-4b06-8a35-e53c8e190258"
$Thumbprint = "07EFF3918F47995EB53B91848F69B5C0E78622FD"
$SiteURL = "https://icewolfch.sharepoint.com/sites/IcewolfDemo/"
$FileURL = "Freigegebene Dokumente/AADExport/AADUsers.csv"
$Tenant = "icewolfch.onmicrosoft.com"
#Connect-PnPOnline
Write-Output "Connect-PnPOnline"
Connect-PnPOnline -Url $SiteURL -ClientId $AppID -Thumbprint $Thumbprint -Tenant $Tenant -WarningAction Ignore
#Get-PnPContext
#Items in Folder
$RelativeURL = "Freigegebene Dokumente/AADExport"
$Items = Get-PnPFolderItem -FolderSiteRelativeUrl $RelativeURL
$Items
#Upload File
$CSVFile = "C:\GIT_WorkingDir\PowerShellScripts\SharePoint\AADUsers.csv"
Write-Output "Uploading CSV to Sharepoint"
$FolderObject = Get-PnPFolder -Url $RelativeURL
$Upload = Add-PnPFile -Path $CSVFile -Folder $FolderObject
If ($Upload -ne $null)
{
Write-Output "File sucessfully uploaded"
}
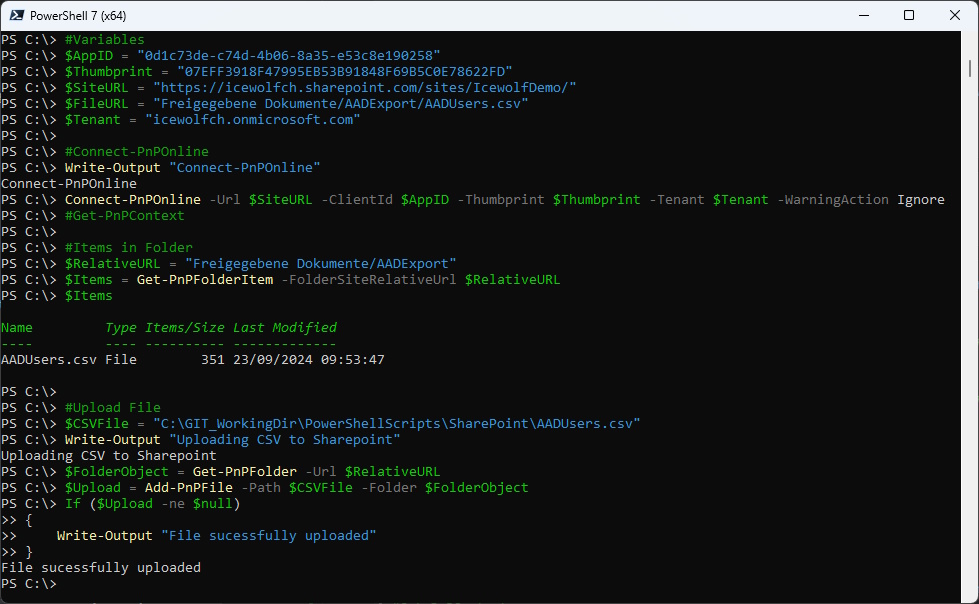
Summary It’s quite a Job to Analyze current ACS and AddIns, then figure out what has to be changed, bevore the Azure ACS can be disabled on the SharePoint Tenant with the DisableCustomAppAuthentication Parameter. It took me a while in my Tenant to understand and adopt. This will even take more Time in an Enterprise with a large Number of SharePoint Sites and Applications that have Access to Sharepoint somehow.
Regards
Andres Bohren
About the Author:

Andres Bohren
Andres Bohren works as a Senior Microsoft Cloud Engineer/Architect for midsize to large Enterprises at isolutions (https://www.isolutions.ch) in Switzerland.
With a robust background in Microsoft technologies, Andres has become a trusted voice in the tech community.
He is renowned for his insightful blog (https://blog.icewolf.ch) and practical PowerShell scripts that help IT professionals optimize their use of M365 and Azure.
Reference:
Bohren, A (2024). SharePoint Online Azure ACS Retirement. Available at: SharePoint Online Azure ACS Retirement – Icewolf Blog [Accessed: 26th September 2024].