When building SPFx webparts which connect to the Graph API, or other 3rd party API’s, you have to grant the appropriate permissions to the ServicePrincipal used by SPFx, which is called “SharePoint Online Client Extensibility Web Application Principal” – see Request permissions to an Azure AD application.
There are a few ways you can do this;
- Declarative permissions request by editing the SPFx solution manifest
- Programmatically using;
Once granted, you can check to see what permissions the service principal has by using the CLI, PnP Powershell or SharePoint Online Mnaagement Shell;
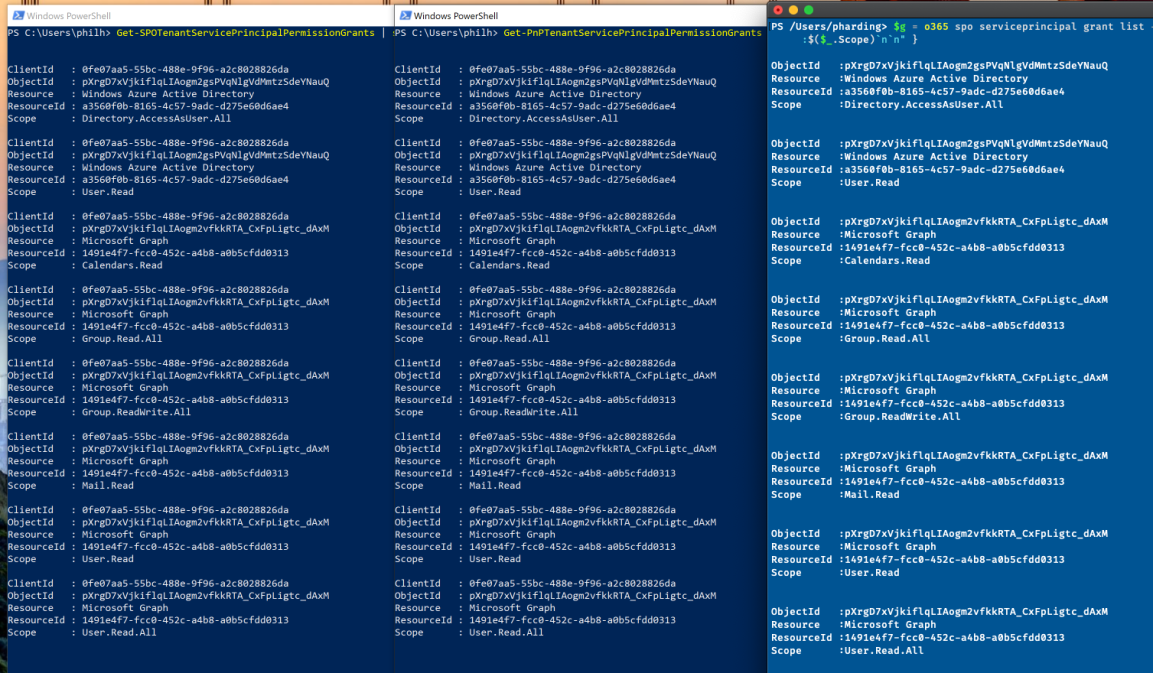
o365 spo serviceprincipal grant list
In the screenshot above you can see I’ve got permission grants for the Graph API and the Azure Active Directory Graph.
What you can also see is that the ObjectId property values are the same for all Scopes belonging to a Resource – the same ObjectId for all scopes for Azure Active Directory Graph and the same ObjectId for all scopes for the Graph API.
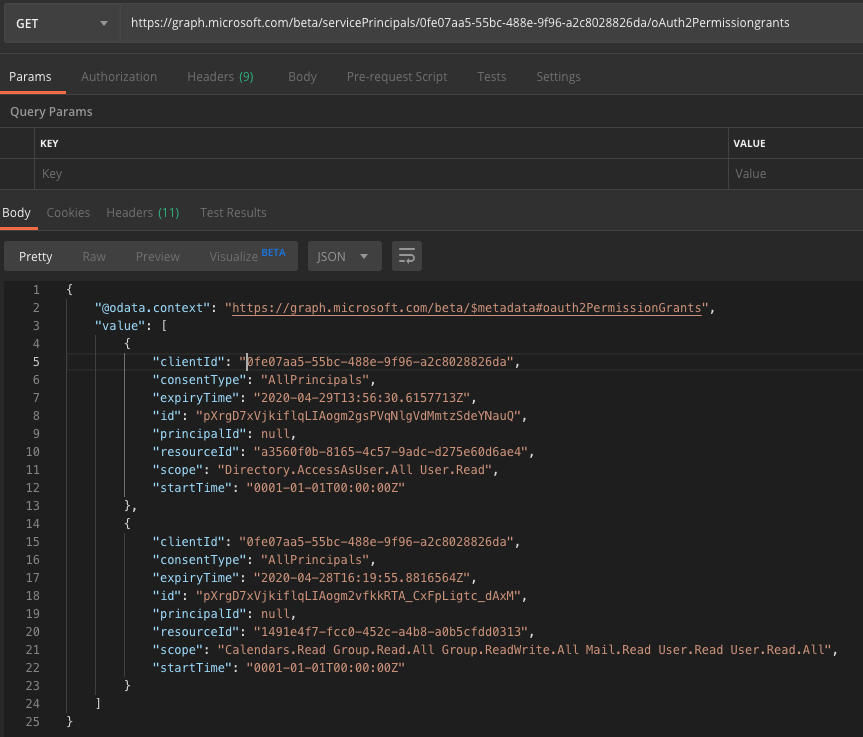
This seems a little odd, but if you check the Service Principal object out using the Graph REST API to get the permissions grants, you’ll see that all grants are actually aggregated into 1 for each unique resource.
https://graph.microsoft.com/beta/servicePrincipals/<servicePrincipalId>/oAuth2Permissiongrants
Should you want to revoke one of the Scopes granted, the documentation for both the CLI and Powershell imply that you can do so by using the unique ObjectId of the Scope.
If you do this;
o365 spo serviceprincipal grant revoke --objectId "pXrgD7xVjkiflqLIAogm2vfkkRTA_CxFpLigtc_dAxM"
For more news check out our resource centre
About the Author:
SharePoint Consultant, Developer, Father, Husband and Climber.
Reference:
Harding. P. (2019). Be Careful Revoking SharePoint SPFx Service Principal Grants. Available at: https://platinumdogs.me/2019/11/01/be-careful-revoking-sharepoint-spfx-service-principal-grants/ [Accessed: 27th October 2020].