How Secure is your Office 365 Ecosystem
So, today’s blog post is going to be focused on the Security and Compliance features in Office 365 so that you folks can understand how secure your Office 365 ecosystem is. It’s a known fact that organizations across the globe are embracing Digital transformation to meet the growing needs and deeds of today’s Cloud first and Mobile first world and Office 365 is playing a vital role in this transformation. Now, if you think about this from a business standpoint, the reason to embrace digital transformation in an organization is wide because it just doesn’t help you to be meet the needs and deeds of your customer, but it also empowers your employees to be more creative and productive. Now, speaking about this I ‘d like to recall a quote from Jeff Bezos (CEO of Amazon) where he says, The biggest threat to successful companies is “…if you won’t or can’t embrace powerful trends quickly. If you fight them, you’re probably fighting the future. Embrace them and you have a tailwind.” I’m pretty sure this makes a lot of sense.
Alright, now speaking about the Security and Compliance features in Office 365, we all know that Office 365 was introduced on 2011 and it has come a long way since then. It has received many major updates as well as many new features and services alongside this journey and today it has turned out to become world’s number 1 SaaS solution and Microsoft has worked hard to keep up this place. The below mentioned image should give you an overview of the current momentum of Office 365 in today’s IT market.
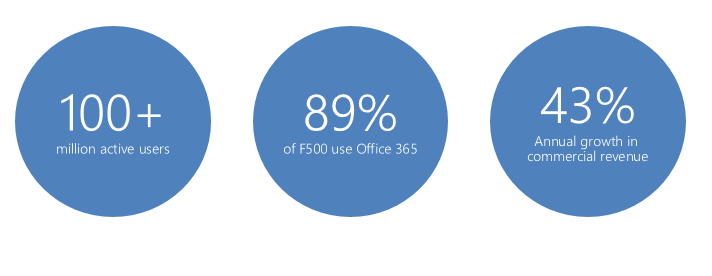
Current momentum of Office 365 in today’s IT market
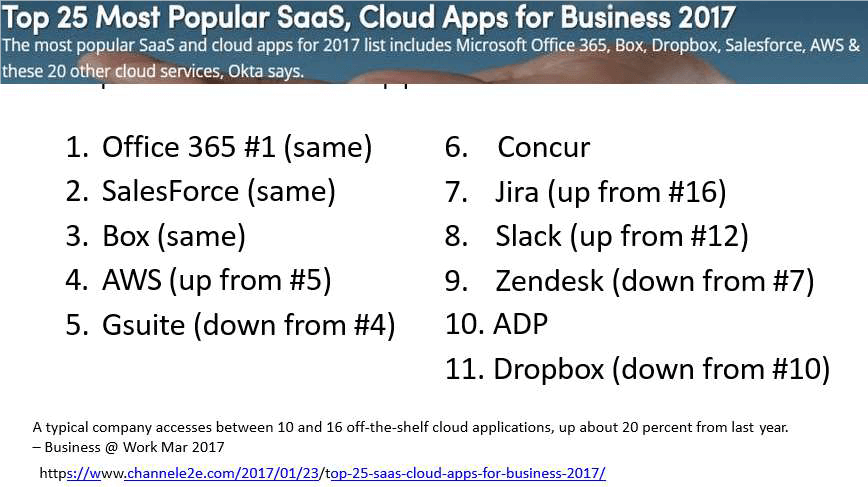
Top 25 most popular SaaS, Cloud Apps for Business 2017
Although, these numbers are great and undoubtfully Office 365 is really a great service. We as customers are always concerned about security because our data is not in our datacenters and instead it’s in Microsoft’s datacenter and there are many other parameters that concerns us. I often hear this from my friends who work as CISO’s in their respective organizations and of course many security folks whom I know in the industry have shared the same vision. So, the burning question in all our minds is …. What about security? How do I ensure that I have not been compromised? How do I make sure that my data is in my control even though Microsoft is the custodian for it? Also in addition to that, today’s security landscape is really scary.

Social media giants frequently get hacked

Security confusion
Moreover, it’s just not that …Earlier when we all had our applications such as Exchange Server, SharePoint Server, Skype for Business server & LOB apps running in on-premises servers in our datacenters we had the concept of firewall which was acting as the security perimeter as shown in the image below.
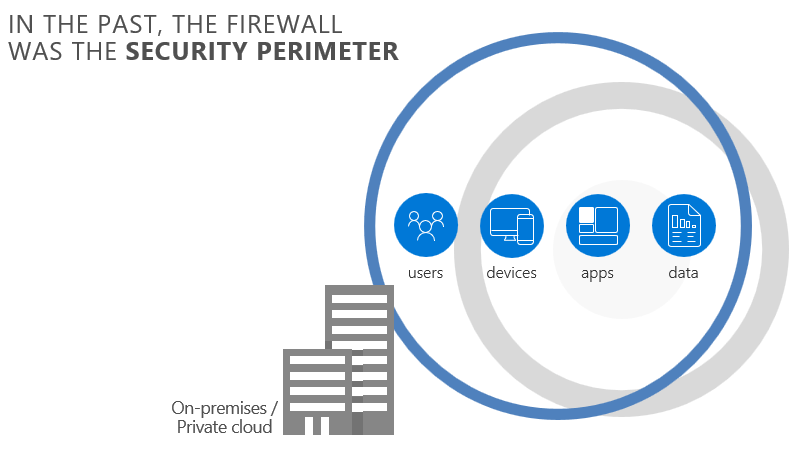
Security Perimeter
Now, with Cloud we have fewer boundaries but more data and more apps which bring in more complexity as shown in the image below.
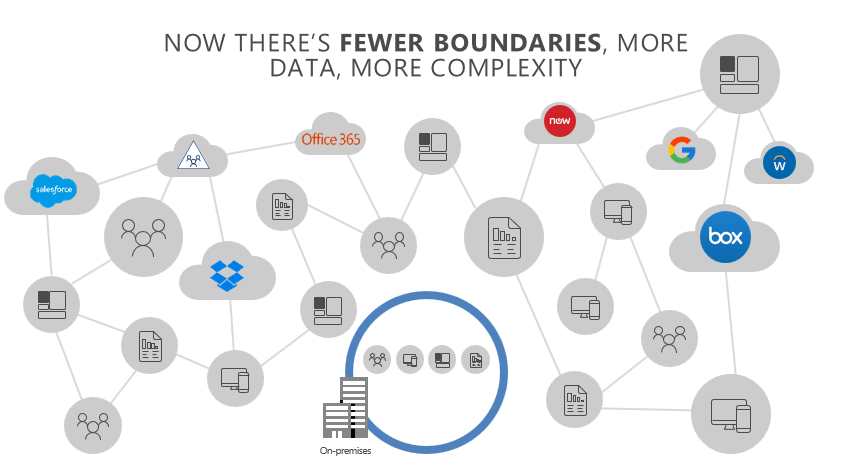
Fewer boundaries more complexity
This of course raises a question in all our minds as decision makers about how can I enable productivity without compromising security? Because all these services which Office 365 offers are really great, but how do I trust the service? How do I ensure that my data is on safe hands?
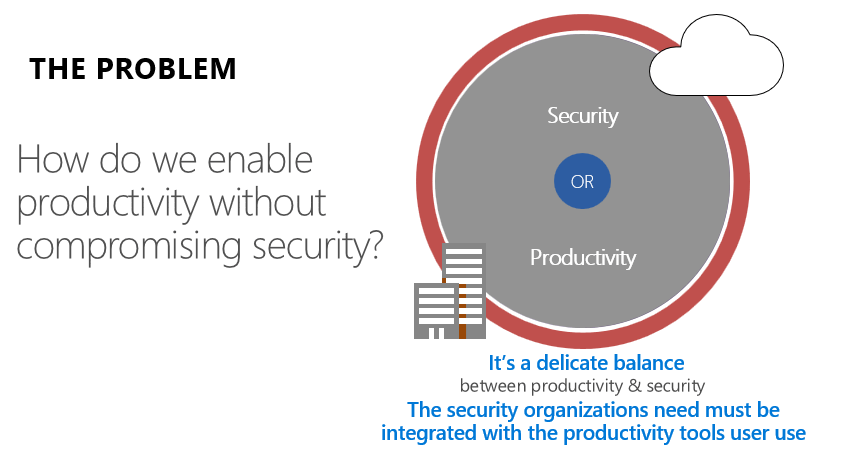
Security or productivity
Well, there are a lot of tools out there that can be purchased for this purpose but then all these tools are meant to solve a specific purpose and they can’t solve all the problems related to security in Office 365. So, it’s quite confusing for the Security folks to decide which tool to buy to ensure that their data is secure. We have a wide variety tools but then they don’t solve all the problems and in addition to that you would also end up in managing all these tools individually which requires a lot of manpower and would often lead to management overhead as well. On top of this the license for all these products could cost you a fortune.
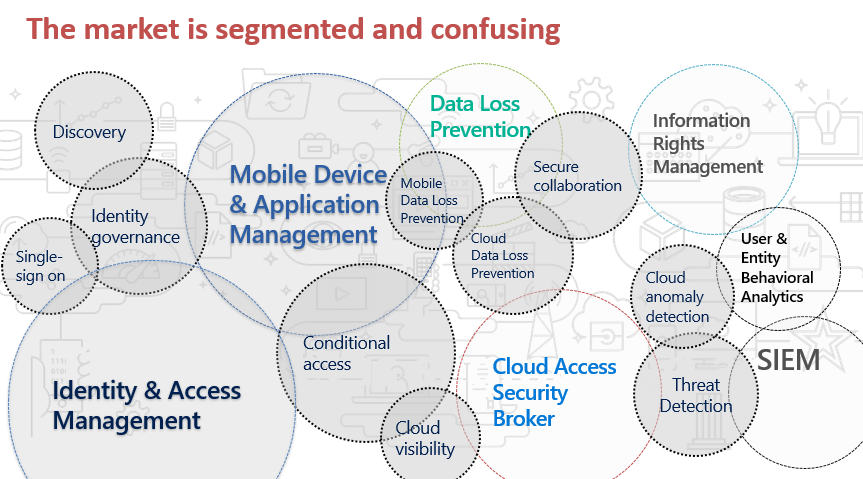
The market is segmented and confusing
So, now that I have lined up all the issues that we face in securing data on a Cloud first mobile first world in front of you folks , I’m going to explain about how to get rid of this and ensure that your data is secure by using all the Security and Compliance features in Office 365.
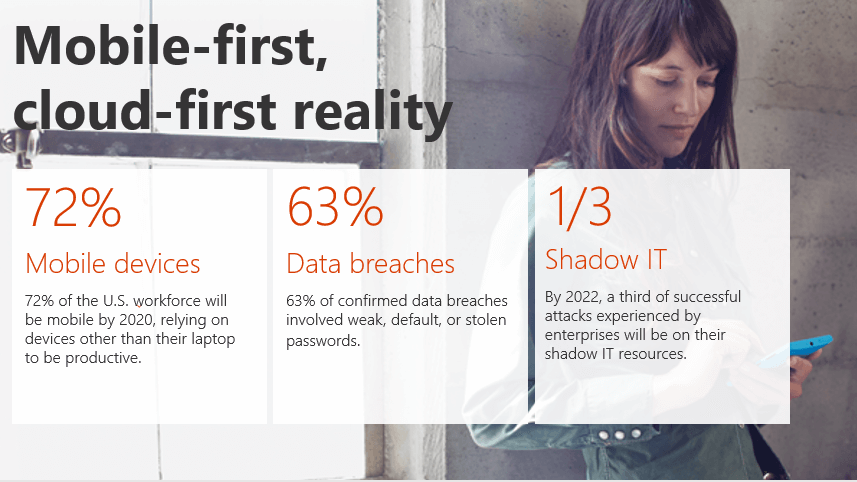
Mobile-first, cloud-first reality
So, this post is mainly meant to showcase the security and compliance features in Office 365 that organizations can count on to ensure that Office 365 is really a trustworthy service and to also make them understand about how they can benefit from these features without purchasing multiple tools. These features that I’m referring to can be a life saver as you can get everything you want as depicted in the image below.

Where to protect
Note: This is going to a series of articles where I’ll be explaining each feature in detail. So initially I’ll begin with giving an overview of all the features and in a later blog post I’ll be getting into the nitty gritty of all the features. Alright, I guess I’ve set the mood now so let’s get started …
Listed below are the areas of focus for Security and Compliance in Office 365 and we have couple of offerings from Microsoft for each of these areas. These services might not really add more value if you use them individually but when it is put together and given to as a service names as EMS (i.e. Enterprise Mobility and Security) it can make wonders.
Note: All the features that I’ll be mentioning below can either be purchased separately or can be purchased together as package called as Enterprise Mobility and Security. EMS is available to us in two flavors as mentioned below
- Enterprise Mobility and Security E3 (aka: EMS E3)
- Enterprise Mobility and Security E3 (aka: EMS E5)
Please go through the link below to understand the licensing details for EMS E3 & E5
https://www.microsoft.com/en-in/cloud-platform/enterprise-mobility-security-pricing
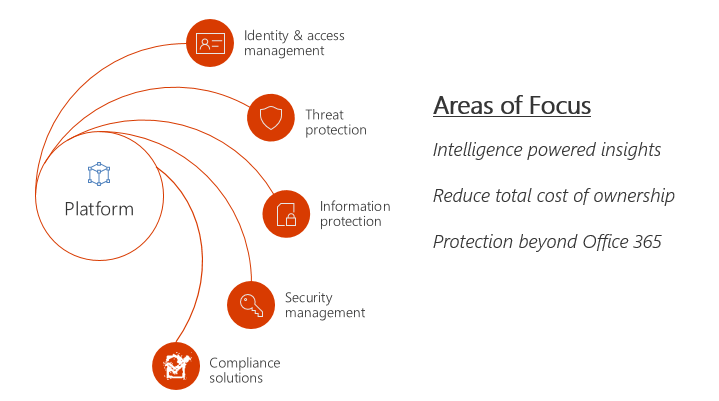
Areas of Focus
The image below should give you an overview of all the offering we have under each area.
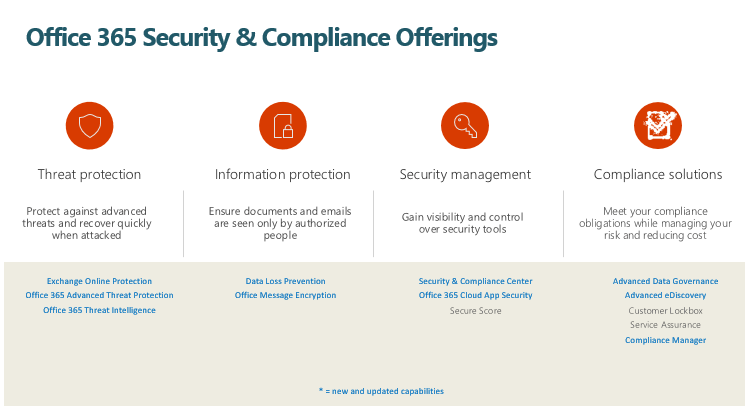
Office 365 Security and Compliance Offerings
Now, let’s jump in and look into these offering individually.
1.Threat Protection:
Listed below are the offerings we have under Threat Protection category
- Exchange Online Protection (aka: EOP)
- Office 365 Advanced Threat Protection (aka : ATP)
- Office 365 Threat Intelligence
- Exchange Online Protection (aka: EOP):
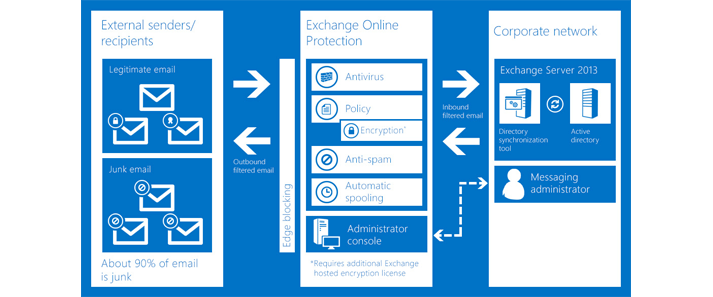
Microsoft EOP
Microsoft Exchange Online Protection (EOP) is a cloud-based email filtering service that helps protect your organization against spam and malware and includes features to safeguard your organization from messaging-policy violations. It sits in front all outlook.com and Office 365 mailboxes and scans all the emails. It can be used for both on-premises and cloud mailboxes.
Listed below are the primary ways of using EOP for message protection:
Standalone scenario: In this method you can use EOP to provide cloud -based email for your on-premises Microsoft Exchange Server 2013 environment, legacy Exchange Server versions, or for any other on-premises SMTP email solution.
With Microsoft Exchange Online (Office 365): By default, EOP protects Microsoft Exchange Online cloud-hosted mailboxes.
Hybrid deployment: EOP can be configured to protect your messaging environment and control mail routing when you have a mix of on-premises and cloud mailboxes.
The below mentioned image should give you an overview of how Exchange Online Protection Mail Flow works.
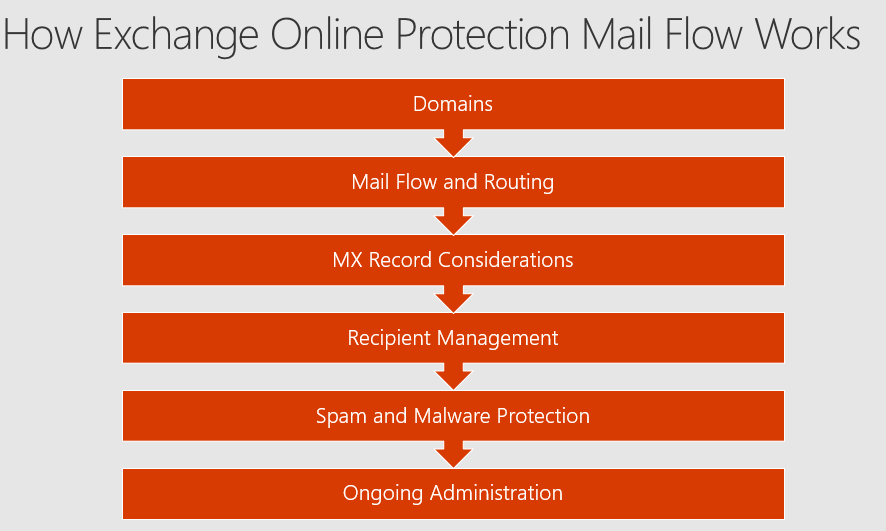
EOP Mail Flow
The below image should give you a high-level overview about how EOP processes incoming email.
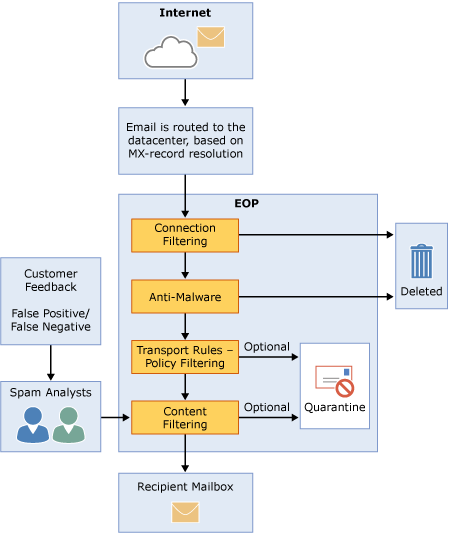
EOP Incoming Mail
Explanation:
- An incoming message from the Internet initially passes through connection filtering, which checks the sender’s reputation and validates the message for malware. Most of the spam is stopped at this point and deleted by EOP.
- Once done the message continues through policy filtering, where messages are evaluated against custom transport rules that you create or enforce from a template. For example, you can have a rule that sends a notification to a manager when mail arrives from a specific sender. (Data loss prevention checks also occur at this point if you have that feature enabled)
- After that, messages pass through content filtering, where content is checked for terminology or properties common to spam. A message determined to be spam by the content filter can be sent to a user’s Junk Email folder or to the quarantine, among other options, based on your settings.
- Finally, after a message passes all of these protection layers successfully, it is delivered to the recipient.
Now, let’s look into how the mail flow works on an inbound scenario, outbound scenario and on Hybrid mode (i.e. online and on-premises together) .
a) How the inbound mail flow works?
- EOP routes email to your on-premises environment via outbound connectors
- Your on-premises email system receives via one or more anonymous receive connectors
- You do not need to configure both inbound and outbound mail flow at the same time
b) How the outbound mail flow works?
- On-premises servers route email to EOP for delivery to the internet by utilizing a smart host. In Exchange, that is a send connector for the * address space. Use the same address as the MX record is for the internet as smart host value
- Configure an inbound connector in Exchange Online Protection to receive emails from on-premises. Configure connector to accept only from your on-premises TLS certificate or configure to receive from your IP range.
- EOP will scan for outbound spam and route to internet via EOP published IP ranges for email or the unpublished “high risk pool” of IP addresses for identified spam
c)How the mail flow works in Hybrid mode?
- Hybrid is a likelihood when you have Exchange Online mailboxes and Exchange Server on-premises
- All email to an Exchange Online mailbox goes through EOP – no direct delivery even with hybrid
Therefore, configure hybrid properly to ensure internal email is treated as internal
EOP Licensing:
- EOP standalone – This service is designed for on-premises Exchange mailboxes.
- EOP in Office 365 – This service is designed for Exchange Online mailboxes in the cloud.
- Exchange Enterprise CAL with Services – This service is much like EOP standalone, but also includes data loss prevention, as well as PowerShell remoting administration capabilities.
Also, please go through this link below to know in detail about EOP licensing.
https://products.office.com/en-us/exchange/exchange-email-security-spam-protection
- Office 365 Advanced Threat Protection (aka: ATP):
Office 365 Advanced Threat protection protects your email, files, and Office 365 applications against unknown and sophisticated attacks. Initially when ATP was launched it was available only for emails. But today , ATP can take care of SharePoint Online , OneDrive for Business , Microsoft Teams and also Office Online .
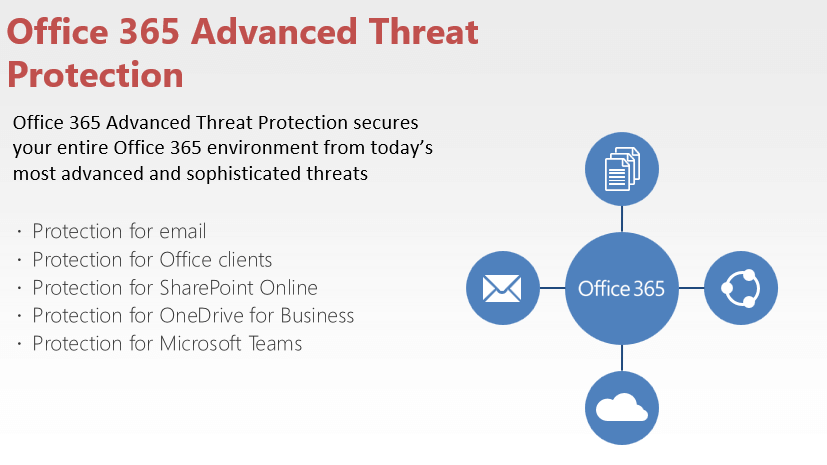
Office 365 Advanced Threat Protection
Listed below are the four pillars of Office 365 Advanced Threat Protection:
- Secure your mailboxes against advanced threats
- Protect against unsafe attachments
- Protect your environment when users click malicious links
- Get rich reporting and track links in messages.
New malware campaigns are being launched every day by attackers, and Office 365 has a solution to help protect your email, files, and online storage against them. Office 365 Advanced Threat Protection can help to protect user’s mailboxes, SharePoint and OneDrive files, online storage, and applications against new, sophisticated attacks in real time. It offers holistic protection in Microsoft Teams, Word, Excel, PowerPoint, Visio, SharePoint Online, and OneDrive for Business. By protecting against unsafe attachments and expanding protection against malicious links, it complements the security features of Exchange Online Protection to provide better zero-day protection.
ii) Protect against unsafe attachments:
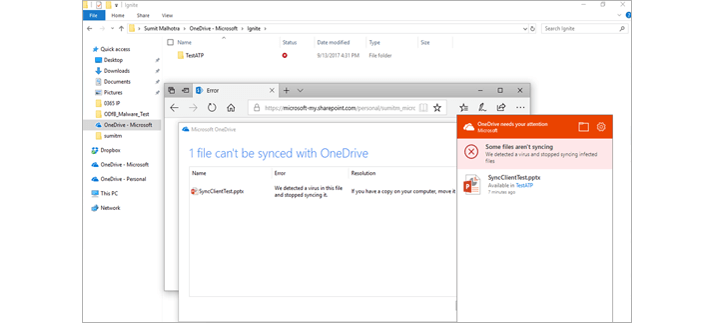
Protect against unsafe attachments
With Safe Attachments, you can prevent malicious attachments from impacting your messaging environment, even if their signatures are not known. All suspicious content goes through a real-time behavioral malware analysis that uses machine learning techniques to evaluate the content for suspicious activity. Unsafe attachments are sandboxed in a detonation chamber before being sent to recipients. The advantage is a malware free and cleaner inbox with better zero-day attack protection. So what basically happens behind the scenes here is , every email gets scanned in the Safe attachment sandboxed environment which is built by Microsoft and the recipient would initially just receive the email body without the attachment stating that his attachment is being scanned and would be delivered in a minute .If the Safe attachment sandboxed environment doesn’t find any malicious content the recipient will receive the attachment in next few minutes , if not the attachment would be quarantined and the Office 365 admin as well as the user would be notified . Also, for any given reason if the attachment which has malicious content in it gets delivered and later MS figures out that it has malicious files in it, even at that point of time ATP can pull back that email despite of it reaching the user’s mailbox.
iii) Protect your environment when users click malicious links:
Exchange Online Protection provides protection against malicious links by scanning content. Safe Links expands on this by protecting your environment when users click a link. While the content is being scanned, the URLs are rewritten to go through Office 365. The URLs are examined in real time, at the time a user clicks them. If a link is unsafe, the user is warned not to visit the site or informed that the site has been blocked as shown in the screenshot above. Reporting is available, so administrators can track which users clicked a link and when they clicked it. In this case, the URL’s gets scanned in the Safe Link virtual environment by Microsoft which is similar to the Safe attachment sandboxed environment that I explained above.
iv) Get rich reporting and track links in messages:
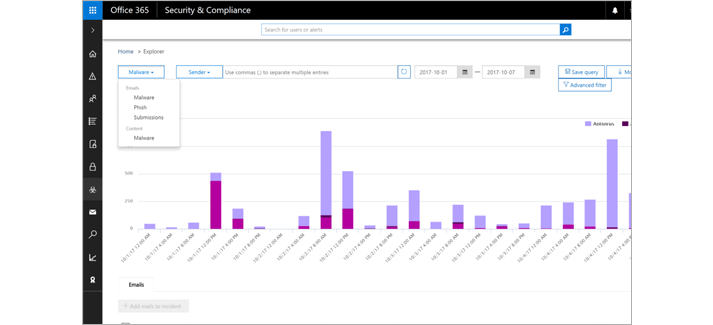
Gain insights
Gain critical insights into who is being targeted in your organization and the category of attacks you are facing. Reporting and message trace allow you to investigate messages that have been blocked due to unknown viruses or malware, while URL trace capability allows you to track individual malicious links in the messages that have been clicked.
The below mentioned image should give you a complete overview about the architecture of Advanced Threat Protection in Office 365.
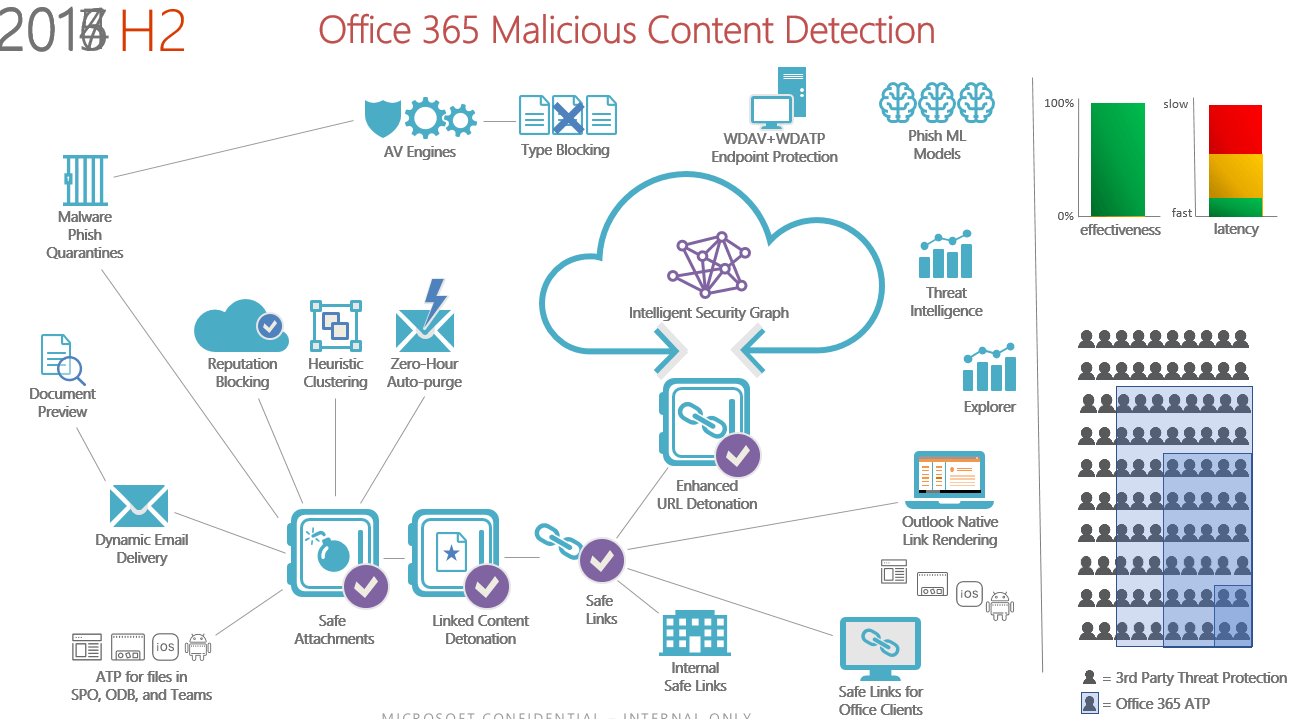
Architecture of Advanced Threat Protection
Purchasing Office 365 Advanced Threat Protection:
You can add Advanced Threat Protection to the following Exchange and Office 365 subscription plans:
- Exchange Online Plan 1 & Exchange Online Plan 2
- Office 365 F1
- Exchange Online Protection
- Office 365 Business Essentials
- Office 365 Business Premium
- Office 365 Enterprise E1
- Office 365 Enterprise E2
- Office 365 Enterprise E3
- Office 365 Enterprise E4
- Office 365 Enterprise E5
- Office 365 Enterprise K1
- Office 365 Enterprise K2
- Office 365 Education
v) Office 365 Threat Intelligence
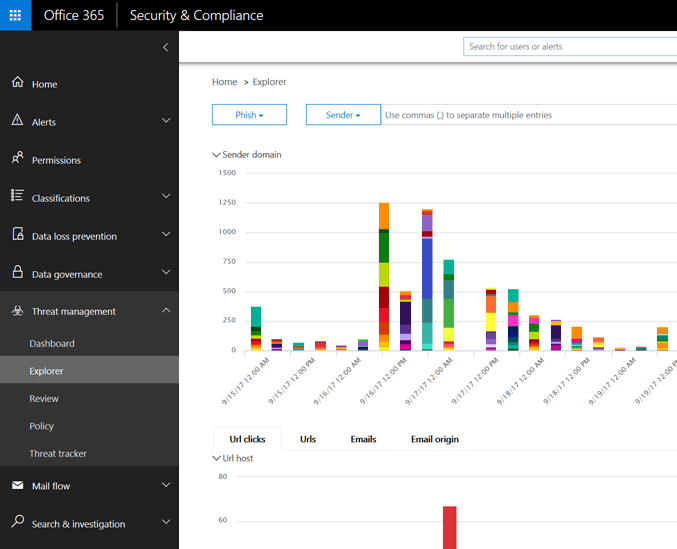
Threat management > Explorer
Office 365 hosts one of the largest enterprise email services and productivity suites in the world, and manages content created on millions of devices. In the course of protecting this information, Microsoft has built a vast repository of threat intelligence data, and the systems needed to spot patterns that correspond to attack behaviors and suspicious activity.
Threat Intelligence leverages the Microsoft Intelligent Security Graph, which analyzes billions of data points from Microsoft global data centers, Office clients, email, user authentications, signals from our Windows and Azure ecosystems and other incidents that impact the Office 365 ecosystem.
So, in a nutshell what’s Office 365 Threat Intelligence? Well, Office 365 Threat Intelligence helps security analysts and administrators protect their organization’s Office 365 users by doing the below mentioned three things ….
- Making it easy to identify, monitor and understand attacks
- Helping to quickly address threats in Exchange Online and SharePoint Online
- Providing insights and knowledge to help prevent attacks against their organization
Now, if you’re wondering about what’s a Microsoft Intelligent Security Graph which I’ve explained above, let me try to explain that below.
The Microsoft Intelligent Security graph is a service built by Microsoft to collect telemetry data generated by all users using Office 365, devices that are connected to Office 365, IP addresses from which you login to Office 365 etc. and they have built an intelligent security graph. Now this basically has Machine Learning and Artificial intelligence built into it so that it studies every user’s behavior in Office 365 (meaning, from where a user logs in often, from which IP address does he/she login, from which country does he login, from which mobile device does he often connects to Office 365 etc.) and for any given reason if it finds an abnormal or anomaly activity from the normal behavior it marks that activity as malicious and takes appropriate security measures. The best part is, all this is done on its own without any human intervention. The below image should help you understand the amount of telemetry data Microsoft collects every month.
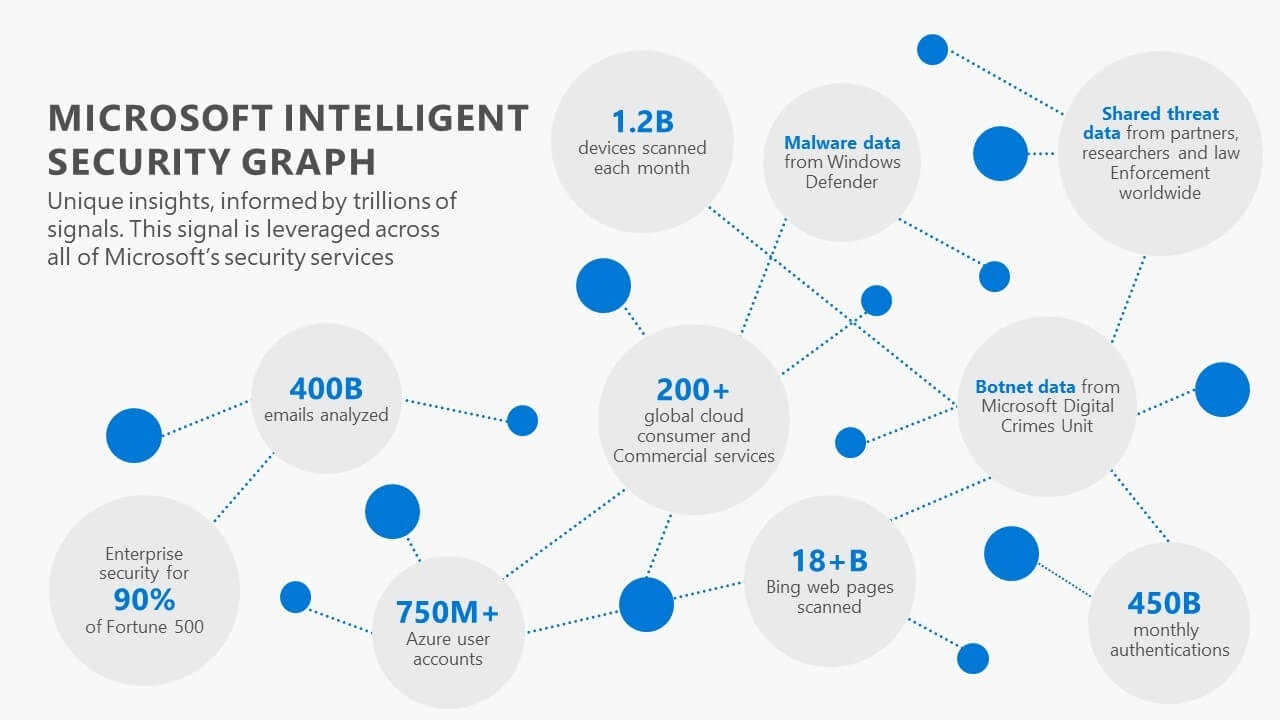
Microsoft Intelligent Security Graph
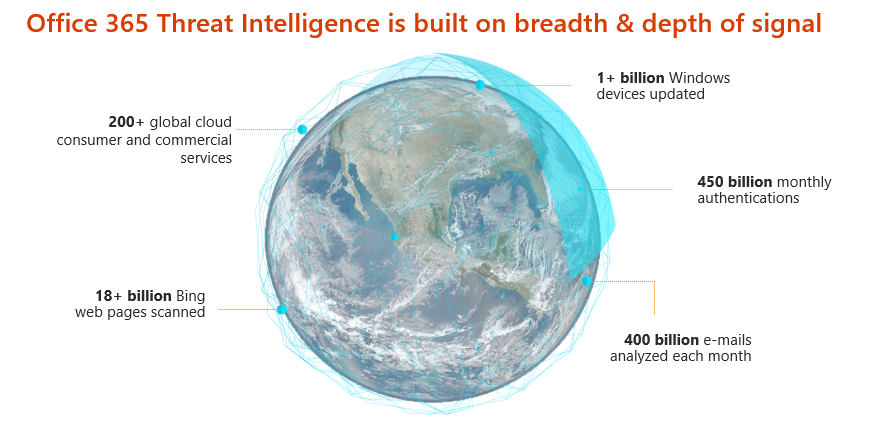
Office 365 Threat Intelligence
Although, this is jaw dropping and sounds bit crazy, there’s a method to this madness. Now, let me try to explain that, the attacks that you see today in a cloud first mobile first world are really very sophisticated and you need to respond to that in minutes and not in hours or days and if your failing to do so the amount damage caused could be really unbearable as attackers out there are getting smarter day by day. So, I’m glad that Microsoft has built the Microsoft Intelligent Security graph for their Cloud services which helps us to be protected. Now based on the signal it gets from a user’s activity the below mentioned actions would be prompted for the user as shown in the image below. Microsoft says that they analyze 10 TB of data every day and this is expected to increase eventually.
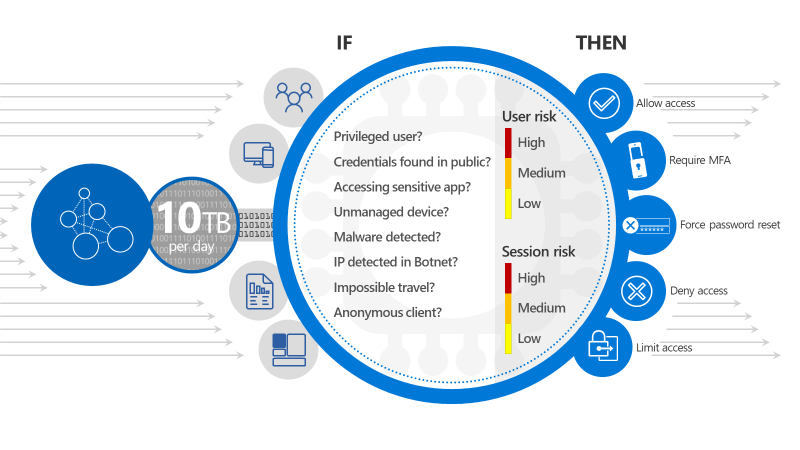
10 TB per day
So, based on the conditions given to it such as (privileged user, unmanaged device etc.) it will grant access to the user. This is called as Conditional Access in Office 365 and I’ll discuss about this in later blog post.
If you’re interested in knowing more about Microsoft Intelligent Security graph, I’d urge you all to go through the below mentioned two links.
http://cloud-platform-assets.azurewebsites.net/intelligent-security-graph/
https://www.youtube.com/watch?v=-Q_G3yF9ZL4
So, what else do we have under Threat Intelligence? Well, we have three important components as a part of Threat intelligence which I want you folks to pay attention to.
- Threat dashboard:
You can use the Threat dashboard (this is also referred to as the Security dashboard) to quickly see what threats have been addressed, and as a visual way to report to business decision makers how Office 365 services are securing your business.
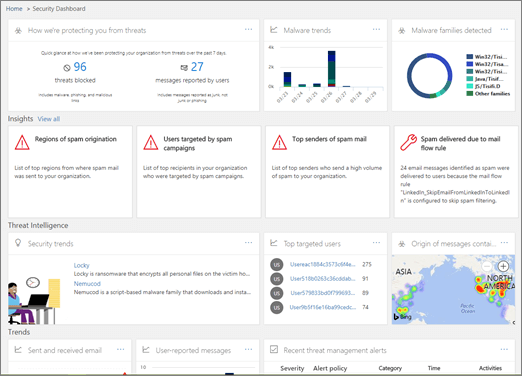
Security Dashboard
To access this dashboard, in the Security & Compliance Center, go to Threat management > Dashboard.
Threat Explorer:
You can use the Threat explorer to analyze threats, see the volume of attacks over time, and analyze data by threat families, attacker infrastructure, and more. The Threat explorer is the starting place for any security analyst’s investigation workflow.
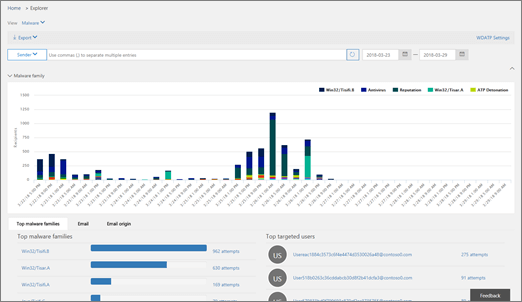
Threat explorer
To access this report, in the Security & Compliance Centerà go to Threat management à Explorer.
Incidents:
You can use the Incidents list to see a list of inflight security incidents. Incidents are used to track threats such as suspicious email messages and to conduct further investigation and remediation.
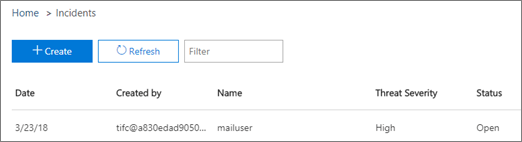
Incidents
To access the list of current incidents for your organization, in the Security & Compliance Centerà go to Threat management à Reviewà Incidents.
Purchasing Office 365 Threat Intelligence:
Office 365 Threat Intelligence is available by default in Office 365 E5 and if you’re using a different plan such as Office 365 Enterprise E3 or Office 365 Enterprise E1, then you can add Office 365 Threat Intelligence as an addon to your existing plan.
Alright folks, that’s all I have for Part 1 and I’ll see you folks on Part 2 …. Good luck in keeping your Office 365 ecosystem secure by utilizing all the features that I’ve described above!!!